November 23 2022 |
SIEM, also known as Security Information and Event Management, is a popular tool used by many organizations to identify and stop suspicious activity on their networks. Although SIEM technology is unquestionably valuable, the solution has some drawbacks, particularly as networks grow larger and more complicated.
You would be well-advised to explore the opportunities that complementary security tools and strategies like NDR and EDR offer if you want to develop a complete and fully functional cybersecurity solution that can address and adequately deal with the growing stack of cyber threats. In this article, we’ll examine SIEM and NDR, and even EDR for context, in more detail and demonstrate how the products could work well together.
In this article, we will talk about NDR and SIEM, how they compare, their benefits, limitations, and how they work together to achieve more robust cybersecurity measures.
What Is NDR?
NDR stands for network detection and Response. NDR’s main function is to keep an eye on network traffic, record any suspicious or malicious activity, and react to any risks that are found. Similar to EDR, NDR employs a set of cutting-edge automated tools to stop cyber incidents, lessen present dangers, fix any potential breaches, and alert the security staff of discoveries within the network. Machine learning is used by NDR, which can be virtual, on-premises, or cloud-based, to recognize both undiscovered and well-known network threats.
How Does NDR Work?
With the help of well-placed sensors, NDR solutions should be able to keep an eye on both east-west and north-south traffic movements. Deep network visibility is provided by this, supporting further NDR solution characteristics such as:
Cyber Incident Detection: NDR systems go beyond signature-based detection by analyzing network traffic using machine learning and data analytics. Due to their ability to recognize patterns and anomalies in network communication, they can detect suspicious or malicious traffic.
Investigation: NDR security systems keep track of network activity and identify patterns that may indicate connections that are atypical or questionable. The NDR system uses this data to automatically respond, and it also provides analysts at the Security Operations Center (SOC) with it so they can more easily conduct incident investigations.
Management of Intelligence: Network detection and response tools should use threat information both inside and outside the company. As part of a converged security architecture, this intelligence may be shared with other security systems in order to help detect potential risks inside network traffic.
Feed Creation: One of the main functions of an NDR solution is to give SOC analysts knowledge of the network’s risks and current security posture. NDR will produce a feed of security alerts identifying potentially harmful and suspicious network traffic.
Threat Prevention: NDR solutions can act automatically and proactively to stop cyber attacks from succeeding in addition to warning security analysts of prospective dangers. Working with firewalls and other security tools to prevent unknown or suspect traffic from reaching its destination can help stop the attack.
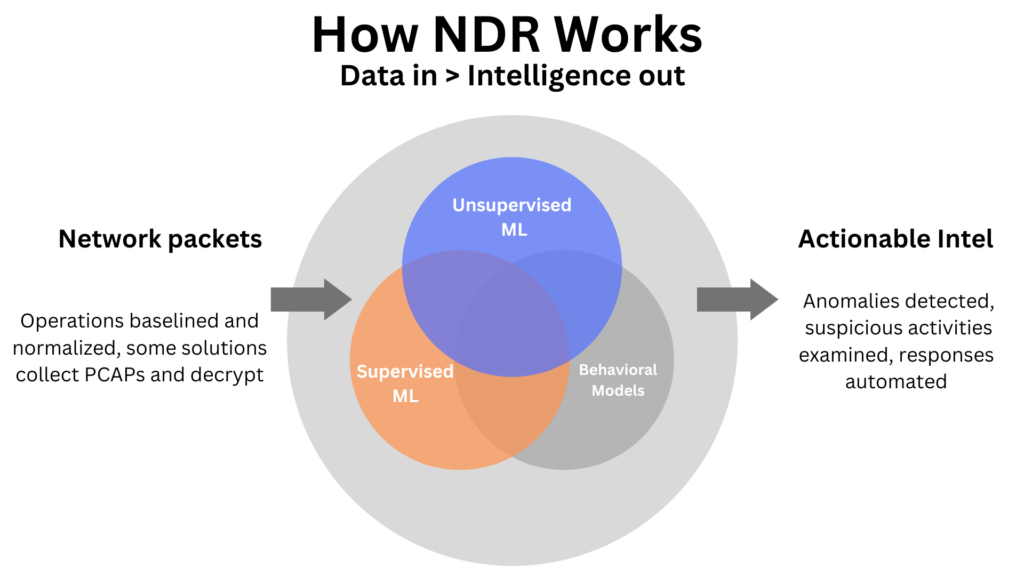
How Does NDR Enhance Your Security?
Traditional network security solutions frequently emphasize detection and employ signature-based detection tools. When the business is being protected against contemporary cyber dangers, both of these are liabilities.
With a detection-focused approach, a security solution looks for potential threats and then depends on a security analyst to handle incident response on the basis of an alert that is created. As a result, swift-moving and automated cyberattacks may have already accomplished their goal before an alarm is seen and a response is triggered. Incident response only takes place after the attack is successful. An automated response capability should be incorporated into an NDR security system so that it can stop an attack before any damage is done rather than reacting after the fact.
Many legacy security solutions, like conventional antivirus software and intrusion detection systems (IDSs), still rely on signature-based detection techniques that are ineffective against today’s threats. The malware used by cybercriminals frequently varies from campaign to campaign, therefore signatures become dated as soon as they are created. In order to recognize and respond to even novel cyber threats for which signatures are still lacking, an NDR system makes use of sophisticated detection capabilities based on machine learning and data analytics.
Benefits Of NDR
The benefits of NDR include:
Eliminate Security Gaps
In general, point solutions like firewalls and EDR do their individual tasks adequately, but there are gaps between each solution’s area of impact that make it possible for threats to elude detection. The final element of this puzzle, network detection, and response, closes these gaps.
Keep in mind that attacks that are challenging to identify typically have the most severe effects. Because of this, keeping out the final 1% of the most severe threats helps small and midsize enterprises avoid catastrophic losses and impacts that could mean the difference between success and absolute failure.
Continuous Threat Detection
The fact that most security tools can be avoided or even disabled is one of their weaknesses. For instance, attackers can get around firewall restrictions by employing a variety of evasion strategies, such as IP spoofing and proxy server use. Attackers can also terminate the programs that are essential for the operation of endpoint security tools like antivirus and EDR. Because cyberattacks always generate traffic, it is advantageous to detect threats at the network layer because they are unable to conceal their activity.
NDR solutions also cannot be turned off because of their design. Attackers won’t even be aware that NDR is watching their actions, making them less cautious. While other security measures could malfunction, NDR offers a consistent and reliable line of defense.
Uncover Threats With Deep Packet Inspection
Over 90% of malware, according to estimates, is concealed in encrypted traffic.1 The only way security technologies might find this kind of malicious code is through deep packet inspection. With firewalls and EDR options, it is possible to achieve this. However, they frequently do it in a way that uses excessive amounts of computational power. On the other side, network detection and response solutions use out-of-band decryption, which doesn’t affect performance. NDR thus offers the visibility required to find vulnerabilities in encrypted data without degrading performance.
Streamline Threat Hunting And Remediation
In addition to helping NDR find threats by correlating traffic throughout the network, it also speeds up forensic investigations following security incidents. Security analysts can track an attack back to its point of entry and identify its underlying cause by being able to link the harmful activity together.
This is essential for threat hunting in order to get rid of any leftover threats and fix any flaws that allowed the threat to enter the system and spread throughout the network, preventing future exploitation of those same flaws.
Protect IoT Devices
The internet of things, or IoT, refers to a group of devices that can connect to the internet but are not traditional electronics like PCs, laptops, or cell phones. IoT devices are becoming more and more common in offices, including smart light bulbs, thermostats, and printers. IoT devices are also being widely used in the industrial and medical fields. The issue with IoT devices is that the majority of them have security flaws and lack the computational power to run endpoint security software.
As a result, threat actors are using IoT devices more frequently to enter networks. As IoT devices are frequently not reported to IT and turn into shadow assets, NDR is able to defend them in two ways: first, by detecting their presence on the network; and second, by spotting unusual activity coming from or going to IoT devices.
What Is SIEM?
Security information and event management, or SIEM (which is frequently pronounced “sim”), is a type of cybersecurity solution that gathers and combines data from various areas of your IT environment with the goal of security monitoring.
SIEMs are centralized log management tools that integrate with all of your systems, servers, and other applications to collect data from each service.
In order to assist with the investigation, early threat detection, and incident response, SIEMs are used for real-time security event analysis. Many data regulatory frameworks mandate that organizations maintain audit logs for up to a year or longer, and they support compliance use cases. However, not all SIEMs are created equal. Without tweaking and ongoing detection rule management, many SIEMs might not be able to perform threat analysis, detection, or response.
How SIEM Works
SIEM includes a set of capabilities that, when combined and integrated, offer full security for enterprises. A SIEM enables a Security Operations Center’s (SOC) incident response capabilities, including threat detection, investigation, threat hunting, response, and remediation actions.
Additionally, by consolidating all of this onto a single dashboard, it is made simpler and more effective. Enterprise visibility, or the ability to see the complete network of devices and apps, is how SIEM offers enterprise security.
An organization’s IT and security framework, including host systems, networks, firewalls, and antivirus security devices, are all sources of event data that a SIEM gathers and aggregates. The program enables security teams to learn more about attacker tactics, methods, and procedures (TTPs) using threat rules generated from knowledge of known indications of compromise (IOCs) and TTPs.
Threats can be found in emails, cloud resources, applications, external threat intelligence sources, and endpoints, according to the threat detection element itself. The goal of SIEM is to give reports and notifications to the right stakeholders within the company when an incident or event has been located, analyzed, and classified. This can involve user and entity behavior analytics (UEBA), which examines actions and behaviors to look for unusual ones that can point to danger. Additionally, it may spot lateral movement, unusual behavior, and hijacked accounts.
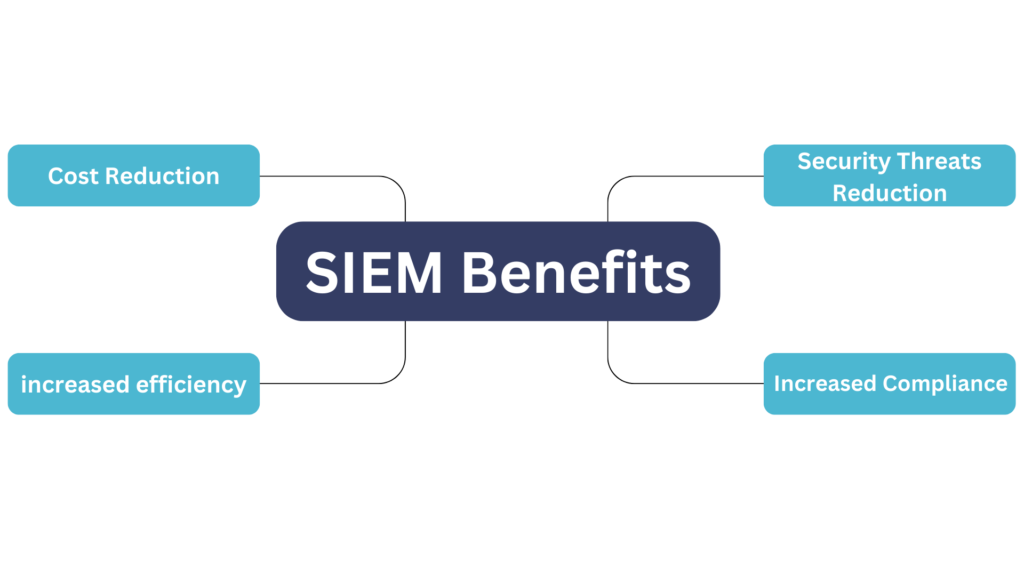
Benefits Of An SIEM Solution
The benefits of an SIEM solution include:
Threat Hunting and Detection
Many of the hosts that record security breaches on your system lack built-in incident detection tools. This implies that while they can record events and create log entries, they are unable to investigate them for any possible suspicious conduct. However, because SIEM technologies correlate and analyze the log data generated across hosts, they are able to identify incidents that may otherwise go undetected—either because the pertinent logs were not inspected or because they were too dispersed among hosts to be noticed.
Cyberattacks are more adept than ever at avoiding detection as they develop in sophistication. A SIEM tool can identify the various components of attacks on the various hosts in your system by collecting and standardizing log data from various systems. For instance, a network intrusion prevention system might detect one aspect of an assault while a computer’s operating system might detect another. The program may then recreate the sequence of events to ascertain the specific nature of the assault and whether it was successful by comparing log data from each host. When a corresponding event is found, the tool can send warnings to the IT team informing them of the entire extent of the attack and directing them to the relevant log data so they can take appropriate action.
Detecting an attack as it is happening versus discovering it after it has already been successful makes a significant difference. The SIEM workflow can reduce the amount of potential damage by spotting issues that might otherwise not be recognized until much later.
Reduced Response Time Using Enhance Situational Awareness
In order to enable quick identification of events involving interactions with dubious or malicious IP addresses, SIEM can make use of the capability of global threat intelligence. Rapid identification of attack vectors and previous interactions speeds up the process of dealing with environmental risks.
Data Aggregation And Visibility
One of the most important advantages of SIEM is the ability to see your complete IT environment. The normalization and correlation of logs in a SIEM solution go hand in hand with this visibility.
Regardless of the size of the company, the IT environment is usually made up of many separate parts, each of which is producing, formatting, and sending massive volumes of data. These parts not only generate a ton of data, but they probably each do it in a unique way. It would take a tremendous amount of time and effort to manually interpret all that data, which is a nearly impossible task that is easily automatable.
For this reason, the data gathering and normalization features of SIEM are extremely useful. A SIEM solution not only gathers and stores the security tool data from your IT environment in a central location, it also normalizes the data into a standard format so you can compare the data with ease. Additionally, the program analyzes and correlates this data, uncovering relationships that enable early detection of security incidents.
Security Staffing And Resources
Staffing security operations teams is an issue in light of the volume and range of threats that are being faced. Using multi-source log data from a single SIEM server, workflow can be streamlined to provide a single report that covers all pertinent logged security events. An analyst-centric user interface provides investigators with more flexibility, easier customization, and quicker reaction times.
Enterprises are still looking for managed services or external service support for their SIEM. Larger clients or partners find SIEM’s threat management appealing for businesses with limited cybersecurity resources.
Simplified Compliance Reporting
Almost every firm, regardless of its size or industry, must adhere to at least some regulations. It can be challenging and time-consuming to make sure you’re adhering to those requirements and that you can demonstrate your compliance. Luckily, SIEM technologies can assist in streamlining the compliance reporting process by gathering, normalizing, and organizing log data. In fact, some firms use SIEMs exclusively to automate compliance reporting since the advantages of SIEM technologies as centralized logging solutions are so great.
The majority of compliance reporting requirements call for detailed, personalized reports that include all pertinent security events that have been logged from all of the hosts in an IT environment. You are unlikely to have effective centralized logging capabilities without a SIEM solution. This implies that you could have to manually retrieve data from each host in your IT system or that you might have to produce separate reports for each host before combining them into a single report. Given that each host in your system is probably logging its data differently, correlation is extremely difficult in the absence of SIEM technologies that automatically normalize your log data.
By streamlining compliance reporting to ensure that MSP customers are not breaking any laws, SIEM technologies can help organizations save time and money. Businesses risk steep fines and loss of accreditation if they fail to provide accurate information to demonstrate compliance. With the aid of SIEM systems, MSPs can quickly provide reports that demonstrate how well their clients adhere to the necessary regulatory standards.
Limitations Of SIEM
SIEM typically gathers, aggregates, and correlates data from various IT and security systems, including host systems, applications, network devices, and security devices. While SIEM systems are capable of identifying and categorizing incident symptoms and performing specific analyses, they have a number of drawbacks.
- Attackers can disable, alter, or delete logs, making them susceptible to tampering.
- Log data storage, extraction, and analysis need a lot of time and resources.
- By definition, log data just contains metadata and lacks the actual data necessary to perform the deeper dive.
- Large volumes of log data that lack slow context searches down without log enrichment.
- Security becomes worn out and distracted by the flood of real and false positives and pointless log data.
The evidence is clear: Endpoint visibility (EDR) and SIEM logs alone are insufficient for a mature security operation. What part is missing, exactly? NDR. In reality, NDR might be the crucial component that completes the picture and increases the efficiency of the other two security measures.
NDR And SIEM, Better Together?
Yes, NDR and SIEM are better together. The outdated strategy of concentrating resources on thwarting an attack at the gate or acting reactively is insufficient. Simply put, adding more firewalls or intrusion detection systems (IDS/IPS) won’t stop the more advanced attackers. It takes more man hours than the majority of businesses to have available to review aggregated logs from a security and event management (SIEM) device, and even then, it is insufficient because log data is insufficient for deep investigation or hunting tasks.
Other systems, such as endpoint detection and response (EDR), offer automatic responses and analyses based on rules that are dependent on what occurs inside the endpoint itself. As a result, stealthy attacks like lateral movement cannot be recognized. Until they are prepared to launch their attack, the attacker will frequently operate in “nearly” stealth mode.
The security team must take numerous steps to combat it successfully, including examining active directory log files, utilizing EDR, enforcing least privilege, collecting logs, and setting up alarms. The fact that no single element can independently identify the attack makes detection and identification a logistical nightmare.
By using traffic analysis to comprehend user/data interactions and going further, a good operator sees the big picture. Additionally, NDR establishes a baseline for “normal” behavior, can warn when abnormal behavior is observed, and can even be precise about what exactly constitutes malicious behavior.
The operator can quickly transition from receiving an alert that lacks context to comprehending the full scope of the incident by visualizing the “tree,” which represents all user/data interactions, and enabling focus on the suspicious ones, the “leaves.”
Not All NDR Are Born Equal
Your security program’s overall maturity can be raised by incorporating NDR. It can be difficult to determine which platform provides the best functionality with the most convenience. This is where WireX Systems comes in.
WireX Systems NDR is concentrating on the investigation to assist your team in moving from alerts and symptoms to diagnostics and remediation, whereas the majority of NDR vendors are concentrating on the detection part to be the first to provide the alert.
The robust platform from WireX Systems addresses important problems that are at the core of conventional network analysis. As previously stated, network security and visibility must focus on internal security threats and extend beyond the network’s perimeter (east-west traffic). However, there are two main obstacles to effectively storing and analyzing mountains of packet data: complexity and capacity.
Only a few days’ worth of payload data could ever be retained when storing information at the packet level (and the rest is high-level metadata). Since the industry statistics for how long it takes to detect an event on average is about 120 day, by the time we would need to use those packets, they would have long since vanished.
The complexity of manipulating “bits and bytes” and turning them into knowledge presents the second difficulty. Even if you had the packets, it would be difficult to use them effectively because most packet-based systems are extremely difficult to operate and will need a network expert and a security expert to operate them.
The key differentiators of WireX Systems revolve precisely around these two problems; WireX offers at least 180 days of payload data along with an automatic analysis that handles the analyst’s labor-intensive tasks.
Contextual CaptureTM technology from WireX Systems provides comprehensive visibility, network analytics, and a deep understanding of the intricate relationships in your network without requiring you to sift through mountains of data. It does away with the need for laborious, impractical processes like raw packet analysis. Months of in-depth network activity and a fully reconstructed OSI stack reveal connections and interactions between network components that would otherwise be hidden from the analyst.
You can respond to threats with decisive context and even find the time to engage in proactive hunting thanks to threat intelligence from Contextual Capture, which enables you to move from alerts and symptoms to diagnostics and remediation.
Contextual capture has ingenious advantages that go beyond providing ample context for detection and response. Traditional network detection tools are struggling to keep up with the massive amounts of data produced by analyzing network traffic, but WireX Systems’ NDR overcomes this problem with Big-Data Analytics, including high-performance databases, lightning-fast response times, and scalability to store many months’ worth of forensics history and intelligence. Your captured activities can be used to visualize, identify, track, and analyze network anomalies so that responses are prompt and focused.
Final Thoughts: NDR And SIEM Your Way, Today
NDR completes the triad by providing visibility into network communications and the particular tasks carried out within those protocols when combined with EDR and SIEM. With next-generation firewalls, it is possible to detect anomalous behavior and activity both at the perimeter and, more importantly, by examining the internal traffic moving laterally. When enhancing log data and endpoint alerts, the NDR’s network insights and artifacts will be used to provide deeper context.
Need robust security for your organization? Speak to us at Wirex Systems today to schedule a demo






