Contextual Capture™
From Packets to Storylines — Real Visibility Without the Guesswork
Contextual Capture™ turns raw network traffic into readable, actionable intelligence — so your security team can stop parsing logs and start solving incidents.
See Everything. Understand Everything. Act Fast.
Traditional tools give you alerts. Contextual Capture™ gives you answers.
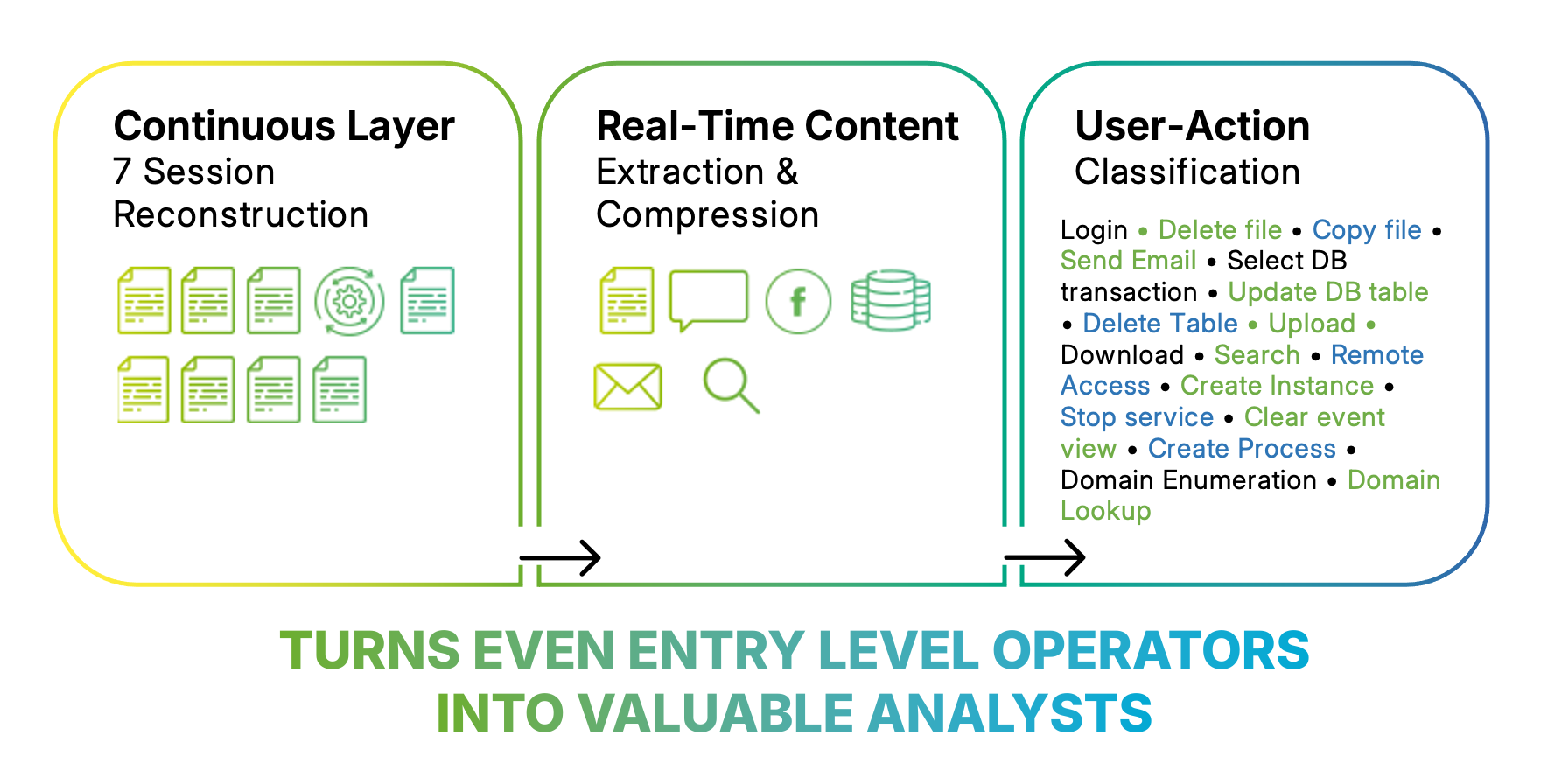
By continuously reconstructing and analyzing thousands of network activities, WireX Systems delivers a clear narrative of what happened, who was involved, and what data was accessed — across cloud and on-prem environments.
Whether you’re investigating a breach, tracking insider threats, or validating compliance, Contextual Capture gives your team the full story, not just pieces of it.
Reconstruct Full User and Data Activity
Stop relying on logs and DPI alone. Contextual Capture continuously collects and rebuilds complete network sessions — including files, database queries, application usage, and user behavior — so you can instantly understand how data is being used or misused.
Smarter Incident Response Starts Here
Contextual Capture doesn’t just collect — it analyzes, correlates, and explains. It’s the foundation of fast, confident response across use cases: