January 7 2023 |
If you’re interested in cybersecurity, you probably already know that the only constant in this industry is change.
To attack your network and endpoints, threat actors constantly evolve their strategies and develop newer, more powerful, and sophisticated techniques. The need for innovation among security professionals led to the development of Extended Detection and Response (XDR) from more conventional detection and response solutions.
Beyond conventional security measures, XDR solutions offer a comprehensive security approach. It analyzes and correlates data from various sources, including endpoints, network traffic, logs from different servers, and cloud applications.
The increased frequency and sophistication of cyberattacks are expected to cause the XDR security landscape to expand over the course of the next few years. Better security is crucial for businesses to avoid the serious repercussions of data breaches and cyberattacks. XDR security is playing a major role in that.
XDR provides a robust, unified security solution that helps you detect, investigate and respond to threats whether they originated from endpoint, network, cloud or some application vulnerability. With XDR, you can rest assured that your data is better protected from any potential threats. If you don’t know what XDR solutions can do for your company or you’re looking to bolster your company’s cybersecurity, this article is for you.
In this article, we will discuss what an XDR solution is, its importance, how it differs from SIEM solutions, and how to choose the best cybersecurity company for your organization.
What Is XDR?
Extended Detection and Response (XDR) is a security solution for detection and response that integrates various security tools and data sources onto a single platform. Endpoints, emails, servers, clouds, and networks are just a few of the security layers that the system collects and correlates data from.
This strategy makes it possible to defend against all types of attacks, including common cyberattacks, network abuse, unauthorized access, insider threats etc., in a more comprehensive and cogent manner. Additionally, it enables your security team to detect, examine, and respond to threats across a number of layers of defense rather than just concentrating on endpoints.
An XDR solution will constantly improve by learning more and more about the threats that are present on the Internet using AI and machine learning. With this type of security solutions, awareness will also increase, productivity will increase, and costs will decrease.
Organizations can get a more complete picture of their security posture with the help of XDR solutions. They can help organizations quickly detect and respond to threats by giving them real-time visibility into their security environment. Organizations can use XDR solutions to identify threats across various systems and networks and take better, or more targeted, action.
As organizations seek out more reliable security solutions, XDR solutions are growing in popularity. They add an extra layer of security for organizations and aid in the quicker and more efficient detection of threats. For organizations looking to mature their security program to handle modern threats, XDR solutions are a potent tool.
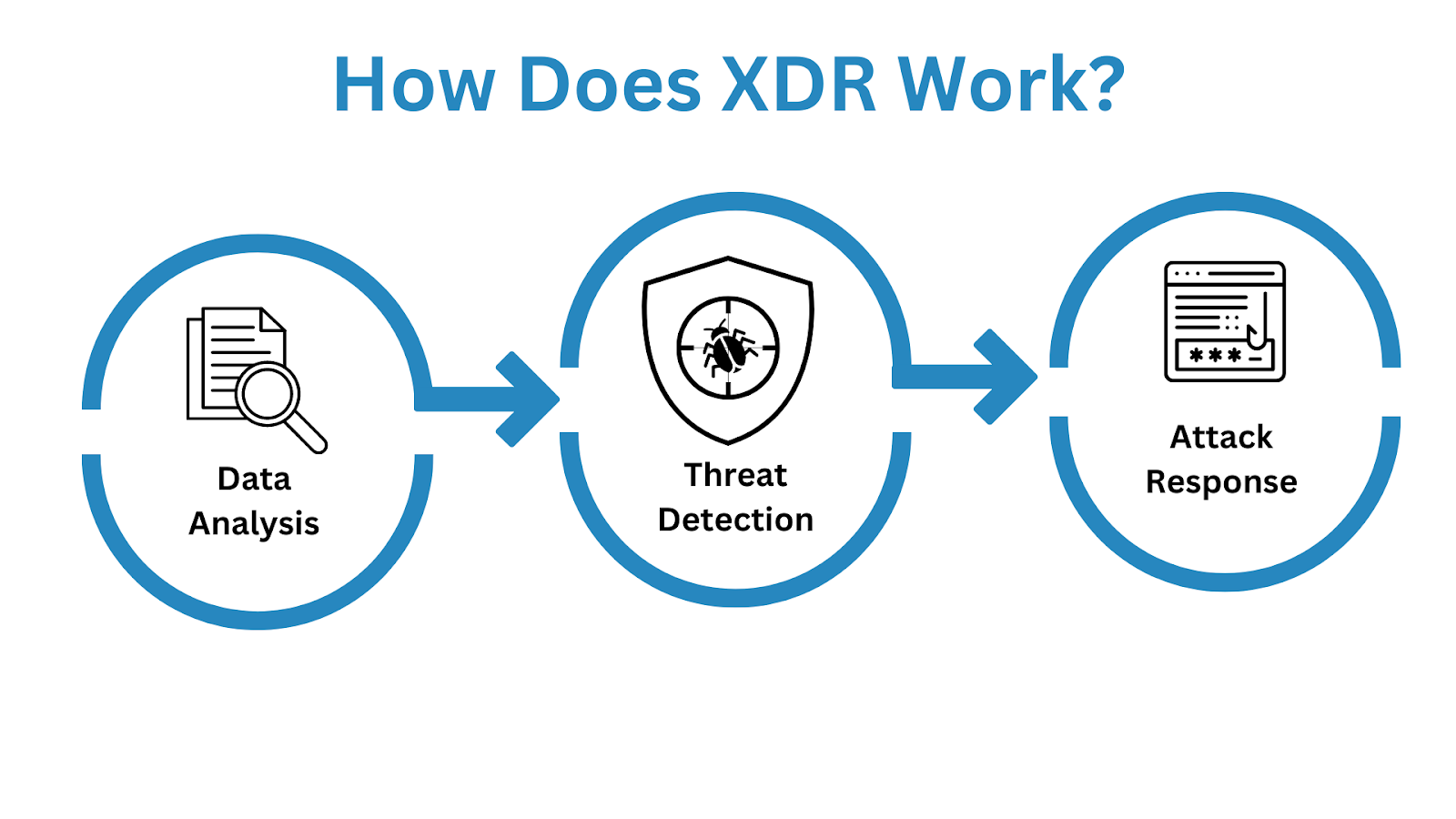
How Does XDR Work?
Extended Detection and Response (XDR) is an advanced security solution that helps organizations detect, investigate, and respond to cyber threats quickly and effectively. XDR works by leveraging a combination of technologies, such as artificial intelligence (AI), machine learning (ML), and automation, to detect threats and respond to them in real-time.
Threat Detection
The core of XDR is its ability to detect threats from a variety of sources, including endpoints, networks, applications, and cloud services. XDR uses AI and ML to identify suspicious activity, such as malicious network traffic, anomalous user behavior, or suspicious file downloads. Once a threat is identified, XDR can automatically take action to mitigate the threat, such as blocking the malicious traffic or quarantining the infected file.
XDR also provides detailed threat intelligence that can be used to investigate threats and understand the root cause of an attack, or the extent of the damage. This intelligence can be used to create more effective security policies, as well as to protect against future attacks.
Data Analysis
EDR, NDR and a variety of logs from different sources including: IAM, DLP, CASB, NGFW and cloud security are among the different layers that XDR fuses into a single data lake in order to accelerate and streamline security operations.
Following a thorough data analysis process, XDR correlates various security alerts from these layers and generates a number of optimized high-priority alerts and security alternatives, sparing security teams from having to fight over alerts and alternatives.
Threat Response
Similar to EDR, XDR has the capacity to continuously identify threats, remove them after detection, and update security protocols to prevent the recurrence of similar attacks.
Additionally, XDR goes beyond endpoint prevention to continuously respond to threats across all security control points, including network and server security as well as container security.
Why Is XDR Security Important?
As cyber threats become more sophisticated, XDR security solutions are becoming more crucial for organizations. Rapid and effective threat detection, investigation, and response are goals of XDR solutions. Organizations can use XDR to gain visibility into threats that might otherwise go unnoticed and take action to safeguard their networks and data.
Similarly, organizations can easily recognize and look into threats thanks to the comprehensive view of their security environment that XDR solutions give them.
They can also gain a better understanding of the threats they face thanks to XDR solutions’ ability to spot suspicious activity across various systems, networks, and applications.This way, organizations can further respond to threats quickly with the help of XDR solutions, giving them a chance to safeguard their networks and data before it’s too late.
By enabling organizations to quickly find and fix vulnerabilities, XDR solutions can also assist them in reducing their attack surface. Organizations can use XDR solutions to detect and look into malicious activity on their networks, which enables them to recognize threats earlier.
Additionally, XDR solutions can help them lower their security costs by enabling organizations to quickly identify and react to threats. By automating many security procedures, XDR solutions can also save businesses time while allowing them to concentrate on more crucial tasks.
Benefits Of XDR
The benefits of XDR are numerous, and they can be extremely valuable for organizations looking to enhance their security posture. XDR helps organizations detect, investigate, and respond to cyber threats quickly and effectively.
Detects More Advanced Threats
Cyberattacks may target your website, DNS, SQL database, URL, and more. Because of this, one key advantage of XDR solutions is traffic monitoring across the entire network, which allows for the detection and blocking of anomalies. Allowing for threats, both old and new, will be recognized and stopped.
Offers More Protection For Multiple Device Sources
XDR has a holistic approach, which means that this technology tracks threats across the traffic of your entire network, in every endpoint, and environment, allowing for the identification of potential risks regardless of their location.
Additionally, since the majority of businesses today operate in cloud environments, this is not disregarded and is effectively monitored and protected by your Extended Detection and Response platform. XDR focuses on your entire attack surface.
Analyzes Data From Several Sources
While observing the traffic, XDR gathers information, analyzes it, and correlates all telemetry. In this manner, abnormal activity can be quickly identified and your security solution has better visibility into your company’s weak points.
Security specialists will be able to triage, identify, and prioritize threats with the aid of this automated analytic feature.
Reduces Alert Fatigue
Because of the automated response, some threats can be dealt with without human intervention. Your IT team will have fewer alerts to sort through and prioritize as a result. This could help decrease the alert fatigue that they may experience, allowing your staff to be more productive in their responsibilities.
Restores Rapidly After An Incident
You can trust your XDR solution to help isolate and mitigate incidents as quickly as possible. Your systems will have less downtime and there will be less chance that other areas will become compromised after the initial infection with the help of an XDR solution.
How Is XDR Different From SIEM Tools?
Extended Detection and Response (XDR) is a relatively new approach to cyber security that aims to provide more comprehensive security coverage and faster response times than traditional Security Information and Event Management (SIEM) solutions. In this section, we will be looking at the differences between XDR and Siem tools.
Scope Of Coverage
The key difference between XDR and SIEM is the scope of security coverage. While SIEM solutions focus on collecting and analyzing log data, XDR solutions are designed to collect payloads information as well both from the endpoint and specifically the network sides, which makes the analytics stored as part of the XDR to be much richer and detailed for both effective response and proactive hunting.
XDR Provides More Advanced Analytics Capabilities
Furthermore, XDR solutions also provide more advanced analytics capabilities than SIEM solutions. XDR solutions use machine learning algorithms and other advanced techniques to identify potential threats and anomalies in data from multiple sources. This allows organizations to detect threats faster and more accurately and respond to them quickly.
More Friendly Solutions
As opposed to SIEM solutions, XDR solutions are made to be more user-friendly, simpler to deploy, and easier to manage in addition to offering more thorough security coverage and advanced analytics capabilities. XDR solutions frequently offer a simple user interface, automated threat detection and response procedures, and real-time awareness of security incidents. Organizations can now detect, research, and react to cyber threats more quickly thanks to this.
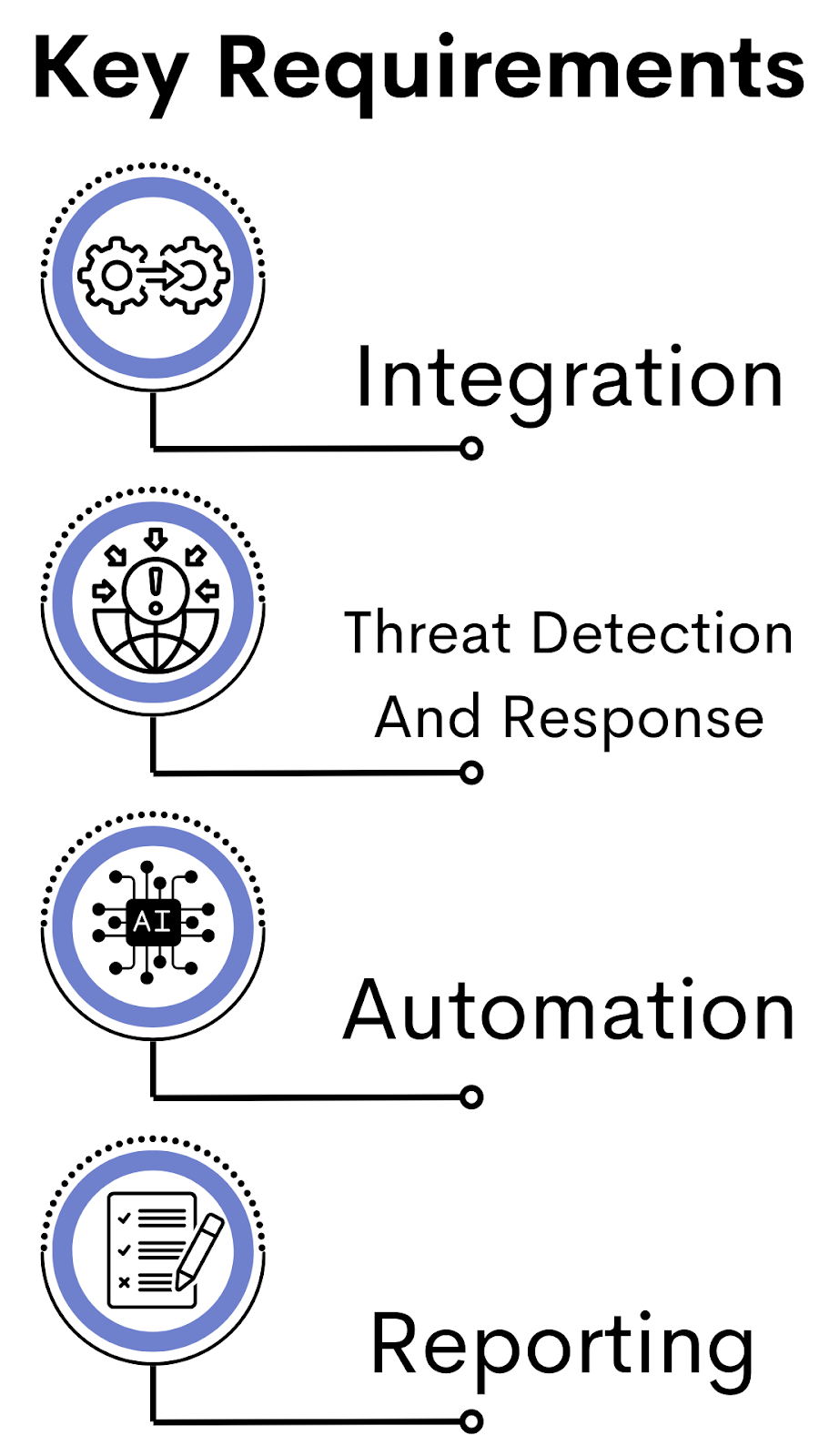
What Are The Key XDR Requirements?
XDR is a powerful security solution that can help organizations detect, investigate, and respond to cyber threats quickly and effectively. However, in order to ensure that XDR is implemented correctly and provides the best possible protection, there are certain key requirements that must be met.
Integration
The XDR platform must be able to integrate with all of your current security tools and systems as the first requirement. This includes any existing security measures you may have, such as firewalls, intrusion detection systems (IDS), endpoint security, and others. This makes it possible for the XDR platform to gather information from each of these sources and provide you with a complete picture of your security posture.
Threat Detection And Response
The second key requirement is that the XDR platform must be able to detect and respond to threats in real time. This means that the platform must be able to quickly and accurately detect malicious activity, and then take appropriate action to contain and remediate the threat.
Automation
The XDR platform needs to be capable of automating threat hunting. Accordingly, the platform must be able to spot suspicious activity and then take the appropriate actions to look into and address the threat.
Reporting
The XDR platform must also be able to produce thorough reports and offer comprehensive visibility into the threats that have been found and the countermeasures that have been applied. This is significant because it enables businesses to monitor the efficiency of their security posture and make any necessary adjustments to improve it.
By meeting these key requirements, organizations can ensure that their XDR platform is providing the best possible protection against cyber threats.
How To Choose The Best XDR Solution
Choosing the best XDR platform for your organization is an important decision. There are a number of factors to consider when evaluating different solutions.
- Threats: First, consider the types of threats your organization is most likely to face. Different XDR solutions have different capabilities when it comes to detecting and responding to specific types of threats. Make sure the platform you choose has the capabilities you need.
- Scalability: Next, consider the scalability of the platform. If your organization is growing, you’ll want to choose a platform that can easily scale with your needs. Look for solutions that offer flexible deployment options, as well as features like automated rule creation and automated alerting.
- Cost: Third, consider the cost of the platform. XDR solutions can vary widely in price, so make sure you understand the total cost of ownership before making a decision.
- Experience: Finally, consider the user experience of the platform. Look for solutions that are easy to use and intuitive for your security team. Make sure the platform you choose has features like a comprehensive dashboard and reporting capabilities. And will aid in the on-boarding of new security personnel – so that the ramp time is not as great as with most SIEMs.
When evaluating XDR solutions, it’s important to consider the specific needs of your organization. Make sure the platform you choose has the features and capabilities you need, as well as a cost that fits within your budget. With the right XDR platform, your organization can stay secure and protected from cyber threats.
FAQs
What is XDR?
Extended Detection and Response (XDR) is a comprehensive security solution that provides an integrated approach to threat detection, investigation, and response. It combines multiple data sources, such as endpoint, network, and cloud security solutions, to provide a comprehensive view of your security posture and help you identify and respond to threats quickly and effectively.
How does XDR work?
XDR works by aggregating data from multiple security sources, such as endpoints, networks, and cloud services, and then analyzing the data to detect and investigate threats. It also provides the ability to automate security responses, such as blocking malicious IP addresses or disabling compromised accounts.
Why is XDR security important?
XDR security is important because it provides a more comprehensive view of your security posture by combining data from multiple sources. This helps you identify and respond to threats quickly and effectively, reducing the risk of data loss or damage.
What are the key XDR requirements?
The key XDR requirements are the ability to automatically collect data from multiple sources, analyze the data to detect and investigate threats, and automate security responses. Additionally, the XDR platform should be able to integrate with existing security solutions and be easy to deploy and manage.
How is XDR different from SIEM tools?
XDR is different from SIEM tools because it provides an integrated approach to threat detection, investigation, and response. It combines data from multiple sources and provides the ability to automate security responses. Additionally, XDR solutions are typically more user-friendly and easier to deploy and manage than traditional SIEM tools.
Why WireX Systems?
Faster Time To Resolution
Ineffective investigation tools mean greater exposure to business risks. The longer it takes to respond to successful attacks, increases the risk of irreversible damage. Security teams cannot afford to waste precious time when trying to understand what is happening in their network. They must arm themselves with better tools to access the information they need, but also save effort and time in the process.
WireX Systems delivers an instant understanding to security alerts while eliminating the heavy lifting of data analysis. The solution’s fast and intuitive interface provides security teams with the necessary intelligence to take action. The security team is empowered to handle more threats in significantly less time, thus shrinking exposure to business risks.
We Turn Everyone In The Security Team Into A Valuable Analyst
Most organizations lack sufficient resources needed to properly investigate every alert. This creates a major bottleneck in the SOC. Organizations must cope with users who lack deep expertise; and allow front-line responders to handle more complex investigations, thus escalating fewer tickets.
Using workflows and knowledge sharing, WireX Systems’ Ne2ition empowers the SOC to handle more alerts and escalate less noise, turning every team member into a valuable analyst. Critical issues will be prioritized for the incident response team, who can then immediately explore in-depth forensics intelligence. The result is an effective investigation process that fully utilizes SOC resources, thus maximizing security operations ROI.
We Translate Network Complexities Into Easy-To-Use Forensic Context
Enterprise companies depend on better context to quickly triage security alerts. However, traditional forensic processes to translate data into intelligence require advanced skill sets only a few team members possess. Enterprise companies need a solution that is easily usable and accessible across teams and comprised of various skill sets – not limited only to the IR expert team.
WireX Systems’ Ne2ition provides comprehensive security intelligence delivered in an actual human-readable form, which can be immediately understood.
This allows security professionals at all levels; security managers, SOC operators, analysts, and incident response teams – to search, view, and interact quickly and intuitively with content-level data without significant manual work requiring deep expertise.
Cyber Security Is Serious Business
While XDR is an important tool in the fight against cyber threats. It is very important to speak to cyber security experts who would analyze your business and proffer a solution that works. WireX Systems’ Ne2ition is shifting the paradigm in incident response with a solution that enables every team member to conduct faster, better investigations while providing automated rich context to reveal the scope of each incident.
The Contextual CaptureTM technology provides immediate context into security alerts, delivering months of in-depth visibility to the world’s largest organizations. By up-leveling skills and creating workflows for knowledge sharing, the solution empowers the entire security team to handle more threats in significantly less time, using the existing tools already deployed, thus maximizing security operations ROI.
Today, leading enterprise companies choose WireX Systems’ Ne2ition as a keystone in their security infrastructure. Learn more at here!.






