January 25 2023 |
What happens when malware enters your applications or ransomware begins to shut down your systems? For the layperson, it may seem like there’s no rhyme or reason to how a managed security service provider works, but there are actual frameworks that go into action when threats are detected.
These are called Incident Response Frameworks, and two of the most commonly used ones are NIST And SANS.
Incident response is a process that organizations use to detect, respond to, and recover from a security incident. It’s a critical part of any organization’s cyber security strategy and should be a top priority. The SANS Institute, a leader in cyber security training and research, has developed an incident response framework to help organizations create an effective incident response plan.
The SANS Incident Response Framework is a six-step process that includes preparation, identification, containment, eradication, recovery, and lessons learned. It provides organizations with the knowledge and tools they need to respond quickly and effectively to security incidents. This framework is designed to help organizations prepare for and respond to cyber incidents in a timely and organized manner.
The SANS Incident Response Framework is based on the NIST Incident Response Framework, but it has some additional steps and components. This article will provide an overview of the SANS Incident Response Framework, including the steps involved and the differences between the NIST and SANS frameworks. It will also provide answers to frequently asked questions about the framework.
What Is Incident Response?
Incident response is the process of identifying, containing, and eradicating a security incident. It is also known as Incident Handling or Incident Management. Incident response is a critical part of an organization’s security program and is designed to protect an organization’s data and systems from unauthorized access or other malicious activity.
The goal of incident response is to quickly identify the source and scope of the incident, contain the damage, eradicate the threat, and recover systems and data to a secure state. Incident response is a proactive approach to security and involves the use of processes, procedures, and tools to identify and respond to security incidents.
When a security incident occurs, the incident response team is responsible for responding to the incident in a timely manner and ensuring that the incident is contained and the threat is eradicated. The incident response team is typically made up of security professionals with expertise in incident response, forensics, malware analysis, and system administration.
Incident response is a complex process that requires a deep understanding of the organization’s security posture and the ability to quickly identify and respond to security incidents. It is important that organizations have an incident response plan in place that outlines the steps to take in the event of a security incident. The SANS Incident Response Framework is one such plan that provides a comprehensive approach to incident response.

What Is SANS?
SANS (Systems Administration and Network Security) is a global leader in information security training, certification, and research. Founded in 1989, SANS is dedicated to helping professionals and organizations stay ahead of the ever-evolving threat landscape.
SANS provides comprehensive, hands-on training courses and certifications in information security and cyber security, as well as a variety of other security-related topics. Through its global network of training centers, SANS offers courses on a wide range of topics, including incident response, forensics, malware analysis, and secure coding.
The SANS Institute also provides a number of resources to help organizations and professionals stay up to date on the latest security threats, trends, and best practices. These resources include blogs, newsletters, webcasts, and conferences.
SANS is also a leader in cyber security research. The SANS Institute has published hundreds of research papers and white papers on topics such as incident response, malware analysis, and secure coding. The Institute also provides a variety of security-related tools, such as the SANS Internet Storm Center, which provides real-time analysis of cyber threats.
The SANS Institute is committed to helping organizations and professionals stay ahead of the ever-evolving threat landscape. Through its comprehensive training and research, SANS provides the knowledge and skills necessary to respond quickly and effectively to security incidents.
What Is A SANS Incident Response Plan?
A SANS Incident Response Plan is a framework that organizations use to respond to security incidents. It is designed to help organizations respond quickly and effectively.. The plan outlines the steps that need to be taken in order to identify, contain, eradicate, and recover from security incidents. It also includes steps to ensure that lessons are learned from the incident and that appropriate measures are taken to prevent future incidents.
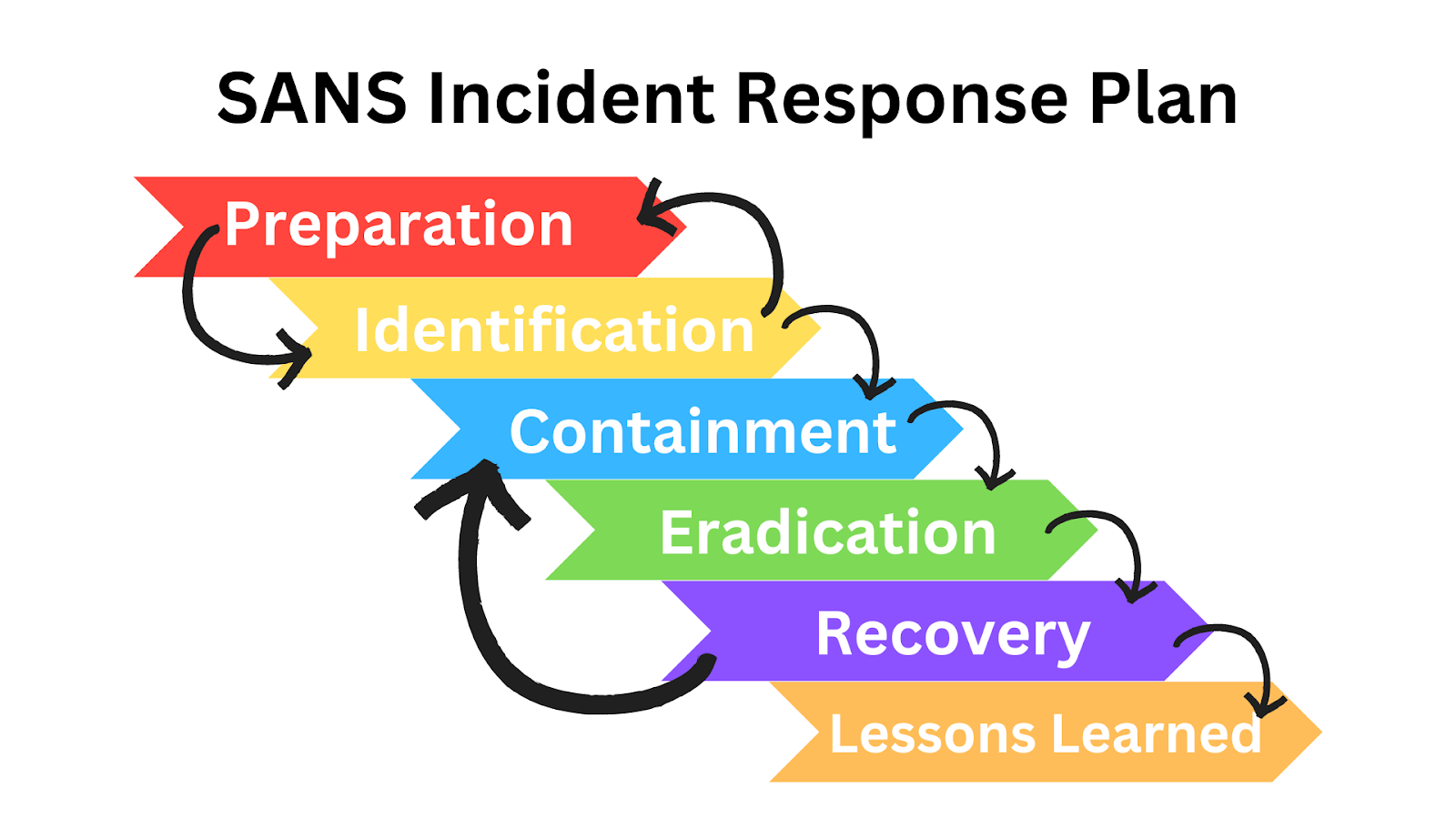
The SANS Incident Response Plan is based on 6 components: preparation, identification, containment, eradication, recovery, and lessons learned.
Preparation: The first step is to prepare for a security incident. This includes creating a plan for responding to a security incident, defining roles and responsibilities for responding to a security incident, and ensuring that the necessary tools and resources are available.
Identification: The second step is to identify a security incident. This includes monitoring for security incidents, recognizing indicators of compromise, and determining the scope and impact of the incident.
Containment: The third step is to contain the security incident. This includes isolating the affected systems, disabling user accounts, and preventing further damage.
Eradication: The fourth step is to eradicate the security incident. This includes removing malicious software, patching vulnerable systems, and restoring affected data.
Recovery: The fifth step is to recover from the security incident. This includes restoring systems to a known good state, restoring data, and validating that the incident has been completely resolved.
Lessons Learned: The sixth and final step is to learn from the security incident. This includes analyzing the incident to identify root causes, assessing the effectiveness of the response, and implementing measures to prevent similar incidents in the future.
The SANS Incident Response Plan provides organizations with a structured approach to responding to security incidents. By following the steps outlined in the plan, organizations can respond quickly and effectively to security incidents and minimize the damage caused by the incident.
Steps To Handling A Cyber Incident
When it comes to responding to a cyber incident, it is important to be prepared and have a plan in place. The SANS Incident Response Framework provides a comprehensive set of steps to handle a cyber incident. These steps include:
1. Preparation: Before an incident occurs, organizations should take steps to prepare for the incident. This includes developing an incident response plan, establishing roles and responsibilities, and training personnel.
2. Identification: Once an incident has occurred, it is important to identify the incident and the affected systems. This can be done by performing scans, reviewing logs, and conducting interviews with personnel.
3. Containment: After an incident has been identified, it is important to contain the incident to prevent further damage. This can be done by isolating affected systems, disconnecting affected systems from the network, and disabling affected accounts.
4. Eradication: Once the incident has been contained, it is important to remove the malicious code or activity from the affected systems. This can be done by using malware removal tools, restoring from backups, and patching vulnerable systems.
5. Recovery: After the malicious code or activity has been removed from the affected systems, it is important to recover the affected systems. This can be done by restoring from backups, reinstalling operating systems, and reconfiguring systems.
6. Lessons Learned: After the incident has been resolved, it is important to review the incident and identify any areas for improvement. This can be done by conducting a post-incident review and updating the incident response plan.
The Difference Between NIST And SANS Incident Response Steps
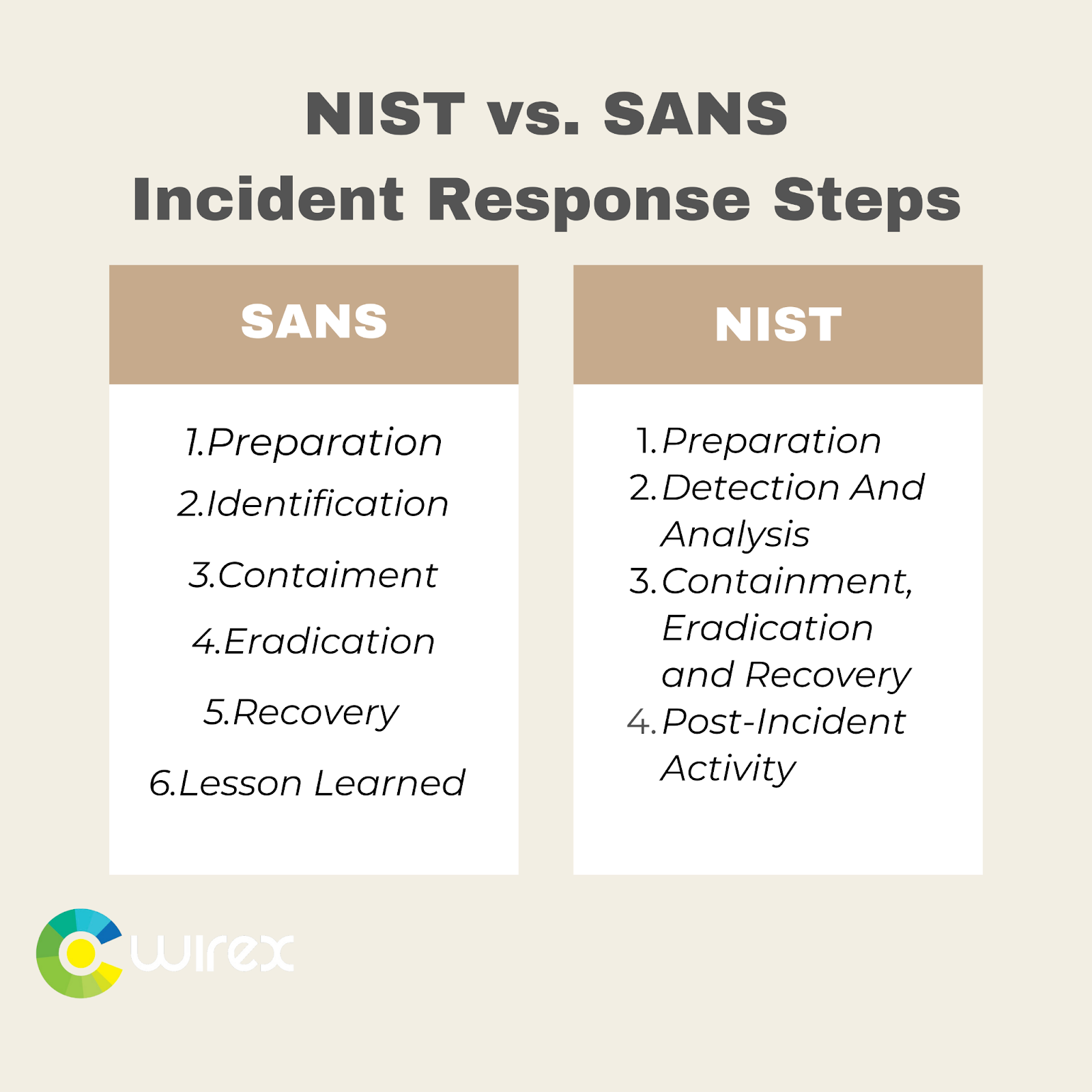
The National Institute of Standards and Technology (NIST) and the SANS Institute have both developed frameworks for responding to cyber incidents. However, there are some key differences between the two frameworks.
NIST’s Incident Response Plan is based on the NIST 800-61 Computer Security Incident Handling Guide. The NIST framework is focused on the process of responding to a cyber incident and provides guidance on how to detect, respond to, and mitigate the impact of a security incident. The NIST framework is more comprehensive in scope and provides detailed steps for responding to a cyber incident.
The SANS Incident Response Framework is based on the SANS Institute’s Incident Response and Forensics Training program. The SANS framework is focused on the technical aspects of responding to a cyber incident, such as how to identify the source of the incident, contain the incident, and eradicate the threat.
In comparison, the NIST framework provides more comprehensive guidance on responding to a cyber incident, while the SANS framework provides more technical guidance on responding to a cyber incident. Both frameworks are important for organizations to understand and use when responding to a cyber incident.
SANS Incident Response Framework Frequently Asked Questions
What is the SANS Incident Response Framework?
The SANS Incident Response Framework is a six-step process that provides organizations with a structured approach to responding to security incidents. The framework includes the steps of Preparation, Identification, Containment, Eradication, Recovery, and Lessons Learned. The goal of the framework is to help organizations respond quickly and effectively to security incidents.
What is the purpose of the SANS Incident Response Framework?
The purpose of the SANS Incident Response Framework is to provide organizations with a structured approach to responding to security incidents. The framework helps organizations to identify, contain, and eradicate security incidents quickly and effectively. It also helps organizations to learn from their experience and implement measures to prevent future incidents.
What are the steps of the SANS Incident Response Framework?
The SANS Incident Response Framework consists of six steps: Preparation, Identification, Containment, Eradication, Recovery, and Lessons Learned. Preparation involves developing an incident response plan and training personnel. Identification involves gathering information about the incident and determining its scope. Containment involves isolating the incident and preventing it from spreading. Eradication involves removing the cause of the incident. Recovery involves restoring systems to normal operation. Lessons Learned involves analyzing the incident and making changes to prevent future incidents.
How does the SANS Incident Response Framework differ from the NIST Incident Response Framework?
The SANS Incident Response Framework is similar to the NIST Incident Response Framework, but there are some key differences. The SANS framework focuses more on the technical aspects of incident response and provides more detailed steps for each stage. The NIST framework is more general and provides fewer steps. Additionally, the SANS framework includes the step of Lessons Learned, which is not included in the NIST framework.
Conclusion
The SANS Incident Response Framework is an effective and comprehensive approach to responding to cyber security incidents. It provides a step-by-step process for incident identification, containment, eradication, recovery, and lessons learned. By following the SANS Incident Response Framework, organizations can ensure that they are prepared to respond to any security incident quickly and effectively. With the right preparation and resources, organizations can ensure that they are well-equipped to handle any cyber incident that comes their way.
For additional information and resources, check out the WireX Systems’ Resource Center. And to see how we solve enterprise challenges with advanced security investigation technologies – head over to our Use Cases page.






