October 10 2022 |
If you’ve had the misfortune to experience a ransomware attack, you are aware of the harm and disruption it can cause to your company’s operations.
Malware, known as ransomware, encrypts data and computer systems and demands payment (often in the form of cryptocurrency) to unlock them. A window asking the user to pay a fine will appear once a computer has been infected. Threat actors frequently assume the identity of a government agency or other authority figure and assert that the system is locked down for security purposes.
This article is an expose on some of what you need to know about ransomware. We will discuss what ransomware is, how it works, who is targeted by the malware, how it impacts your business, signs of attack, and how to prevent an attack.
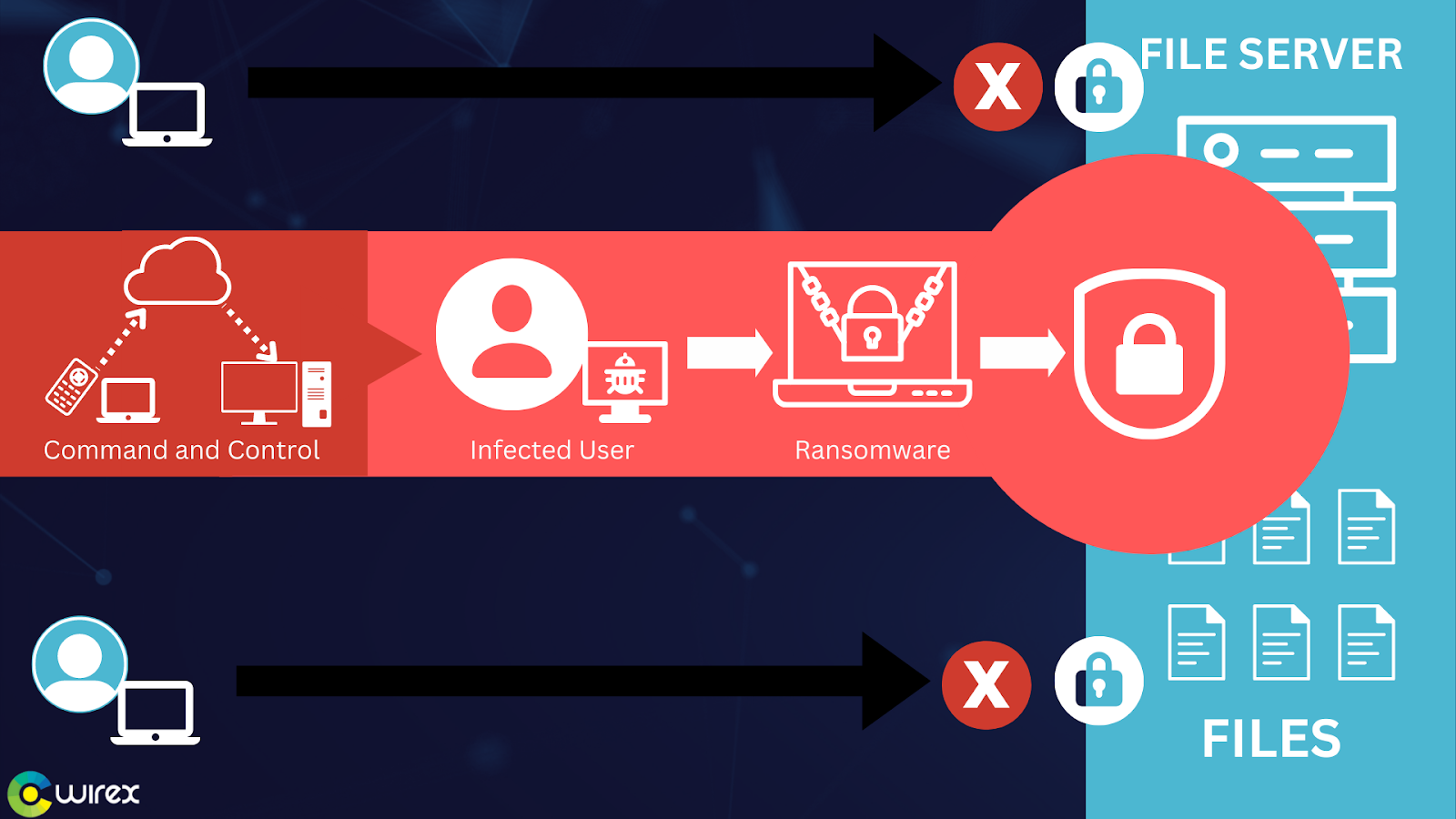
What Is Ransomware?
Ransomware is a type of malware that prevents users from accessing their personal or system files and demands a ransom payment in exchange for access. Although some might believe “a virus locked my computer,” ransomware is more commonly referred to as a type of malware than a virus. The first ransomware versions were created in the late 1980s, and they demanded payment by postal mail.
Today, ransomware authors demand payment via cryptocurrency or credit card, and attackers target different types of people, companies, and organizations. Ransomware-as-a-Service, or RaaS, is a practice where some ransomware authors provide their services to other online criminals.
How Does Ransomeware Work?
Asymmetric encryption is used by ransomware. A pair of keys are used in this type of cryptography to both encrypt and decrypt a file. The attacker generates a unique public-private key pair for the victim, with the private key being used to decrypt files kept on the attacker’s server. Only after the ransom is paid does the attacker release the victim’s private key, though recent ransomware campaigns have shown that this is not always the case. It is nearly impossible to decrypt the files that are being held for ransom without the private key.
Ransomware comes in a variety of forms. Ransomware (and other malware) are frequently spread through targeted attacks or email spam campaigns. To make an endpoint its home, malware needs an attack vector. Once its presence is confirmed, the malware remains on the system until its purpose is served.
After a successful exploit, ransomware drops and runs a malicious binary on the compromised system. Then, this binary searches and encrypts valuable files, including databases, images, and documents. In order to spread to other systems and possibly across entire organizations, the ransomware may also take advantage of network and system vulnerabilities.
Once files have been encrypted, ransomware notifies the user that they must pay a ransom within 24 to 48 hours in order to unlock the files; otherwise, the files will be permanently lost. The victim is forced to pay the ransom to recover personal files if a data backup is not available or if those backups are also encrypted.
Can Ransomware Spread Through Wifi?
Yes, ransomware can infect computers via wifi networks. Whole networks can be disrupted by ransomware attacks that snoop through wifi, with disastrous business repercussions.
In the same way that a computer worm spreads across wifi networks, malicious code that translates to ransomware can also do so. An entire office building could become infected with ransomware if it crosses wifi boundaries.
Make sure computers are secure, patched, and protected to stop the spread of ransomware in this manner.
Use secure passwords on your devices, in particular. For instance, the ransomware Emotet can quickly and easily crack passwords before lateralizing across wifi connections.
What Are Signs Of A Ransomware Attack?
You can be made aware that cybercriminals are in your network and preparing to launch a ransomware attack by looking out for a number of warning signs. You can regain control and minimize actual damage if you can recognize these warning signs and recognize an attack in its early stages. It requires the appropriate equipment and some awareness of potential dangers.
Keep an eye out for these six ransomware attack warning signs.
Suspicious Emails
The majority of ransomware attacks arrive as email attachments. In this situation, it’s important to make sure you’re utilizing a sophisticated email filtering and monitoring solution that not only flags suspicious emails but also informs the administrators of why the email was flagged. An administrator should be notified, for instance, if an email contains an attachment with the file extension “.zip” or “.exe,” as this is almost certainly a malicious attachment.
This gives them the opportunity to caution their staff and urge caution on their part. Of course, you can’t watch over a worker’s personal email account, but you should keep an eye on their work email accounts, especially if they belong to privileged users.
When an email is sent from a public email domain, such as Gmail.com, administrators should also be informed. Your solution should ideally be able to spot grammatical errors as well. Furthermore, it should look for misspelled domain names, dubious HTML components like buttons, and messages and attachments containing words like “invoice,” “FedEx,” “financial statement,” “notification,” and so forth.
Unexpected Network Scanners
Be wary of network scanners that suddenly appear and aren’t needed by your business, especially if they’re located on servers.
Cybercriminals will frequently take control of one computer to launch a ransomware attack. From there, they will probe your network to learn more about the computer’s domain rights and other potential access points. Installing a network scanning tool like Advanced Port Scanner or AngryIP is one way for a cybercriminal to do this. Undoubtedly, a network scanner can be a useful tool. If no one else on your IT team is using a network scanner, check with them to see if they are and raise the alarm.
Unauthorized Access to Active Directory
A hacker may attempt to infiltrate your company’s Active Directory (AD) and gain domain access around the same time they install network scanning software. These tools include BloodHound and AD Find.
For instance, BloodHound uses an ingestor called SharpHound that is available as a PowerShell script or command-line.exe. Its objective is to gather data on AD users, groups, and computers and to map the privilege escalation paths to the domain administrator.
Well-known ransomware variants, like Ryuk, hacked AD servers using Microsoft Remote Desktop Protocol (RDP), then they inserted the ransomware into the AD logon script. This infected everyone who logged into that AD server.
End users can access files and programs stored on a server in an organization remotely using Microsoft’s Remote Desktop Protocol (RDP). However, as more and more employees start working from home, RDP is increasingly being used by attackers to spread ransomware, making it one of the most common attack vectors.
Attackers typically begin by using open-source port-scanning tools like angry or Advanced Port Scanner to search the entire Internet for exposed RDP ports. The attacker will then attempt to log into the network using credentials they have stolen or brute-forcing their way in.
Mimikatz and Microsoft Process Explorer
Given that Mimikatz is one of the most frequently used hacker tools, its presence should always raise an alert. Cybercriminals can steal login credentials and passwords by using the open-source credential-gathering tool Mimikatz. It is frequently used along with Microsoft Process Explorer, a reliable tool that can dump LSASS.exe, a Windows process in charge of enforcing the security system. Penetration testing (also known as ethical hacking) can ensure that Mimikatz-using attackers cannot access your systems.
In contrast to Mimikatz, some hackers employ more subtle methods of credential theft. For instance, Cobalt Strike is a platform that employs a variety of strategies to avoid detection by antivirus software and occasionally imitates widely used programs like Gmail and Bing. While collecting credentials, Cobalt Strike leaves a few traces on an infected system.
Software Removal Programs
The next step for an attacker after gaining administrative rights is typically to disable or remove security software, such as antivirus defenses. They frequently employ reputable software removal tools like IOBit Uninstaller, GMER, PC Hunter, and Process Hacker to accomplish this.
These tools will be found on the network by a logging program. If you find these tools, you should consider their sudden appearance. Software removal programs, on the other hand, are a later ransomware warning sign; they frequently show that hackers have admin-level privileges. In order to stop ransomware from starting up, if you notice software removal, you must take action quickly—within 15 minutes or less.
Who Is Targeted By Ransomware?
Initial victims of ransomware when it first appeared (and then reappeared) were individual systems (aka regular people). However, when they started targeting businesses with ransomware, cybercriminals started to grasp their full potential. Because ransomware was so effective at disrupting businesses’ operations and causing data and financial losses, its creators focused the majority of their attacks on them.
By the end of 2016, ransomware accounted for 12.3% of all enterprise detections worldwide, while only 1.8% of consumer detections were ransomware. A ransomware attack affected 35% of small and medium-sized businesses in 2017. The threat will still exist in 2020 when there is a global pandemic: Ransomware gangs target hospitals and other healthcare facilities, and they’ve developed new extortion techniques like “double extortion,” in which the attackers can demand more money by threatening to leak private information than by unlocking the computers they’ve encrypted. Using the Ransomware-as-a-Service, or RaaS, model, some ransomware organizations provide their services to third parties.
Geographically, ransomware attacks continue to target western markets; the top three targets are, in order, the UK, the US, and Canada. Ransomware writers, like other threat actors, follow the money, so they search for regions with both widespread PC adoption and relative wealth. Expect to see an increase in ransomware (and other types of malware) in emerging markets in Asia and South America as their economies grow.
What Are The Four Types of Ransomware?
The four types of ransomware are:
Crypto Ransomware
Crypto ransomware is one of the earliest and most typical types of ransomware. It works by identifying valuable files on a system and encrypting them to render them useless. Following a ransomware payment demand, hackers will (theoretically) give businesses the decryption key required to unlock their files.
Such ransomware may target specific file types or attempt to infect all files on a device. Some variations can even spread to shared or networked drives, cloud storage, or even devices other than the devices themselves, potentially affecting every aspect of a business. However, they typically leave the device functional.
As businesses become more aware of the threat posed by ransomware and take more preventative measures, this kind of attack is becoming less frequent. For example, having thorough off-site backups can be a good way to lessen the harm done by this kind of ransomware. The hackers who do still use these tools, though, have begun to thwart these initiatives by timing the infection of backups with their malware.

Locker Ransomware (Screen Lockers)
Since it completely locks users out of a system and frequently leaves them with nothing but basic mouse and keyboard inputs to allow them to pay the ransom, locker ransomware can be more disruptive than crypto-ransomware.
In these situations, people may turn on their device to find nothing but a lock screen with instructions for paying and a timer to create a sense of urgency, along with the warning that the device will become permanently unusable if the ransom is not paid.
There is less likelihood that users will lose data if the ransom is paid and access is granted because this type of ransomware typically targets systems rather than using files. However, it prevents businesses from operating normally, just like crypto-ransomware, and many businesses might feel they have no choice but to pay the hackers in order to restore functionality.

Scareware
Scareware is an evolution of more traditional social engineering-based attacks that try to convince people into paying money to fix a problem that doesn’t exist with their computer. In its most common form, malware will repeatedly pop-up alert users that their device has a virus and encourage them to download expensive ‘antivirus’ software to remove it. This will, at best, have no effect, but it is much more likely that it will just introduce new malware to the system.
Although it is debatable whether scareware should be classified as ransomware, many of these attacks have the potential to be very disruptive, either by flooding the screen with alerts or, in some cases, by introducing elements of locker ransomware to disable functionality. Therefore, the impact will be the same for the majority of victims because systems will be disrupted until payment is made.
Effective cybersecurity training is crucial in preventing this kind of attack because this tactic frequently relies on exploiting human emotions. It is crucial to make sure all employees, regardless of their level of technical knowledge, can recognize the warning signs of these attacks.
Double Extortion Ransomware
Double extortion ransomware is one of the most popular ransomware tactics used today – and one of the most dangerous. It functions by encrypting systems and stealing data from networks. Criminals have more clout when it comes to demanding ransom once they have access to this data.
Hackers frequently threaten to publicly release data if a ransom is not paid by a particular date, which is a common method of double extortion. Doxware is another name for this particular type of ransomware. Additionally, hackers might threaten to alert regulators or stakeholders to the breach, which would have negative effects on a company’s finances and reputation. This is done to increase the risk of not paying as well as the time pressure.
There is even a ransomware subtype called triple extortion that aims to put even more pressure on companies to act quickly. A threat of an additional attack, such as a Distributed Denial of Service (DDoS) is one way to achieve this. In addition to the threat of data exposure, the possibility of additional organizational disruption can serve as an additional incentive for businesses to make payments. There is a need for sophisticated, all-encompassing solutions to combat these types of ransomware. To stop this kind of ransomware, Anti Data Exfiltration (ADX) technology is essential in addition to solutions like perimeter defenses and backups. This keeps hackers from obtaining access to the confidential files they require to run this type of ransomware by keeping an eye out for data exfiltration on your network and blocking file transfers.
How To Prevent Ransomware Attacks
Fortunately, there are many ways to guard against becoming infected with ransomware. Because technology is always changing, it’s crucial to follow fundamental cybersecurity procedures and maintain a proactive attitude to ensure that neither you nor your company will ever be at risk from ransomware threats.
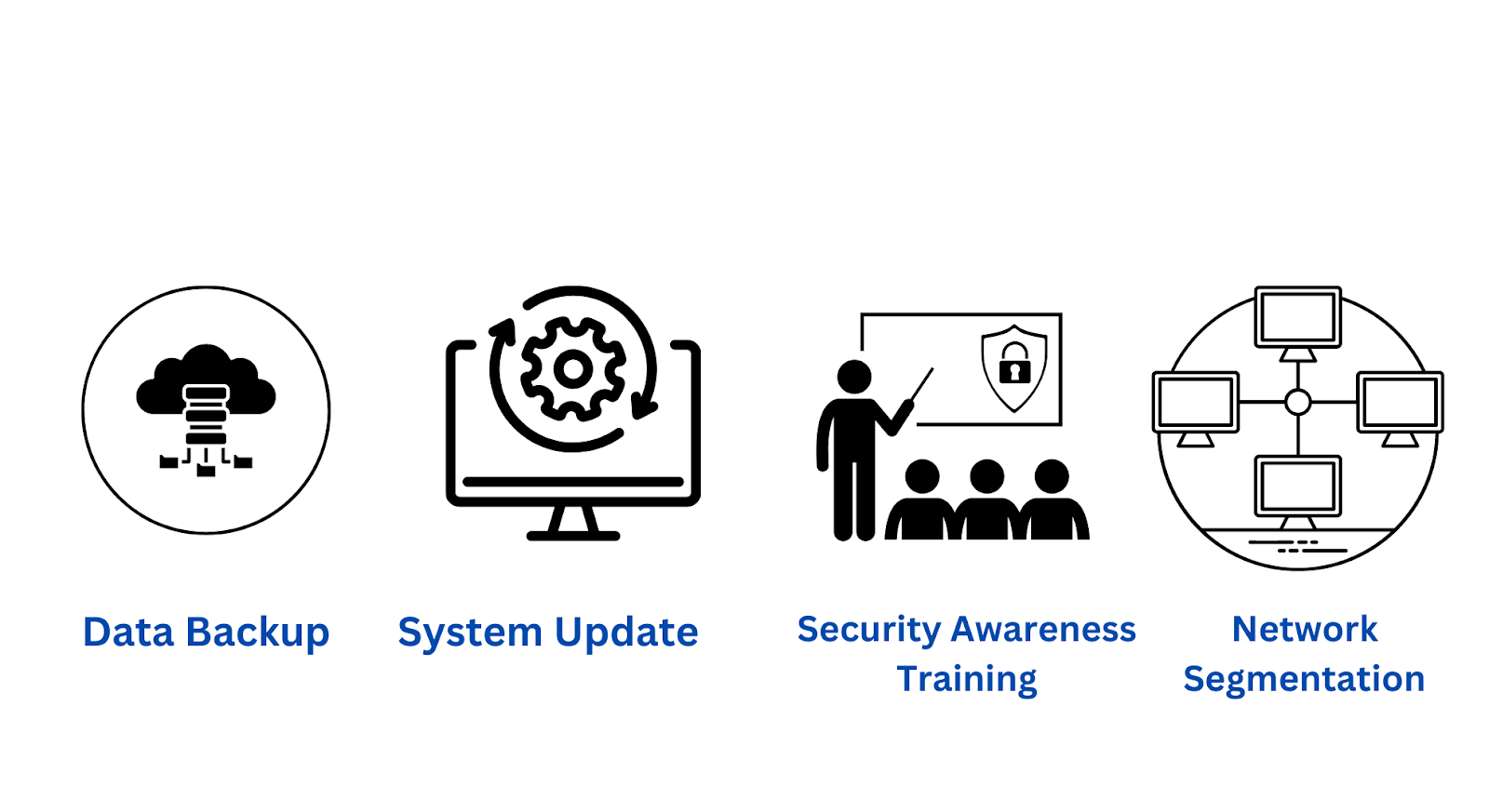
Have Backup For Your Data And Secure Them
One of the simplest risk mitigation techniques is backing up your data to an external hard drive or cloud server. The user can completely clean the computer after a ransomware attack and reinstall the backup files. Ideally, businesses should be regularly backing up their most crucial data.
The 3-2-1 rule is a common method to use. Try to keep 3 distinct copies of your data, 2 of which should be offline, on 2 different types of storage. By including one more copy on an immutable (cannot be changed) and indelible (cannot be deleted) cloud storage server, you can also add another step to the process.
Keep All Systems And Software Updated
Always use the most recent version of your operating system, web browser, antivirus program, and any other software you use. You should make sure everything is patched and up to date because malware, viruses, and ransomware are constantly evolving with new variants that can get around your outdated security features.
Larger companies that rely on dated legacy systems that haven’t been updated in a while are a common target for attackers. The ransomware attack known as WannaCry in 2017 that left major corporations across the globe paralyzed is arguably the most infamous. Even Spanish telecommunications giant Telefónica and Apple chip supplier Taiwan Semiconductor Manufacturing Co. (TSMC) were forced to halt operations for four days as a result. Over 230,000 computers worldwide were impacted in total.
Computers running out-of-date versions of Microsoft Windows were the target of the attack. A recent patch that would have stopped the spread of malware was released, but many users and organizations were slow to update and fell for the scam as a result. Security professionals from all over the world have urged businesses to update their systems as soon as possible since this incident.
Implement Security Awareness Training
Every employee in your company should receive regular security awareness training so they can recognize and avoid phishing and other social engineering scams. To ensure that training is being followed, conduct tests and drills on a regular basis.
Network Segmentation
In the event of an attack, it’s critical to limit the spread of ransomware as much as possible because it can quickly infect a network. By implementing network segmentation, the organization can isolate the ransomware and stop it from spreading to other systems by dividing the network into several smaller networks.
To stop ransomware from reaching the target data, each individual subsystem needs to have its own security measures, firewalls, and unique access. Segmented access will not only stop the threat from spreading to the main network, but it will also give the security team more time to find, contain, and get rid of the danger.
Can You Remove Ransomware?
Yes, it is possible to remove ransomware. Nobody wants to see a ransom message on their computer because it indicates that a ransomware infection was successful. At this point, an organization must decide whether to pay the ransom fee or take other action in response to an active ransomware infection.
How To Mitigate An Active Ransomware Infection
Many successful ransomware attacks are not discovered until after the data has been encrypted, and a ransom note has appeared on the screen of the infected computer. The encrypted files are probably beyond saving at this point, but the following actions must be taken right away:
Quarantine the Machine: The machine should be quarantined because some ransomware variants will try to infect other computers and connected drives. By denying the malware access to additional potential targets, you can control its spread.
Keep the Computer Running: File encryption can cause a computer to become unsteady, and turning off a computer can cause the loss of volatile memory. Keep the computer running to increase the likelihood of recovery.
Create a Backup: With some ransomware variants, files can be unlocked without paying the demanded ransom. Create a backup of any encrypted files on a removable drive in case a fix is discovered down the road, or the files are damaged during an unsuccessful decryption attempt.
Check for Decryptors: See if a free decryptor is available by contacting the No More Ransom Project. If so, try using it to restore the files on a copy of the encrypted data.
Ask for Assistance: Backup copies of files stored on computers are occasionally kept. If the malware has not deleted these copies, a digital forensics expert might be able to recover them.
Wipe and restore: Use a fresh operating system installation or backup to restore the computer. By doing this, the malware is removed entirely from the device.
How Does Ransomware Affect Your Business?
The financial aspect of the ransom itself is the most obvious effect of ransomware, but that is only half the battle. Systems need to be restored, and cybersecurity precautions need to be strengthened. Additionally, there is the productivity loss brought on by downed systems and the attention needed to fix it. A 2020 Sophos Report estimates that the average cost of a ransomware attack without paying the ransom is $732,520.
The truth is that ransomware frequently succeeds, and businesses frequently pay the fee to simply resume operations.
Paying the ransom, however, doesn’t always lead to the restoration of operations; additionally, it can encourage criminal activity and result in significant compliance violation fines. In fact, paying the ransom can make the cost of the ransomware attack double; the same Sophos Report estimates that the average cost to a company that paid the ransom was $1,448,458.
No matter how you slice it, a security team’s worst nightmare is being infected with ransomware.
Final Thoughts: Security For You And Your Site
Technology and the cybersecurity measures that guard it both need to advance. Any person or business should prioritize developing a ransomware defense strategy. Without it, users and organizations who are not adequately protected run the risk of losing sensitive information.
That data is frequently a company’s most valuable asset. Losing it might result in irreparable harm that would render the entire business unusable. It’s critical to maintain a proactive attitude and use the best ransomware protection techniques before potential threats have a chance to exploit you.
To better track any potential threats, why not head over to WireX Systems, where we understand your pain of tracking and help you do the heavy lifting through automation.






