December 28 2022 |
Cybersecurity and abbreviations go together like peanut butter and jelly. It is hard to imagine one without the other. New technology inevitably begets new terms to keep track of.
Still, the industry’s ever-growing acronym soup of abbreviations and jargon can make it challenging to compare technologies over time. Take the example of three closely related categories of threat detection technology: Network Detection and Response (NDR), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR). Each offers a comprehensive solution to detect and respond to various cyberattacks. Moreover, they rely on similar but different approaches worth considering as the volume and sophistication of attacks continue to grow, and the risks to organizations show no signs of relenting.
In this article, we will look at these cybersecurity solutions, why your business needs them, and the differences between them.
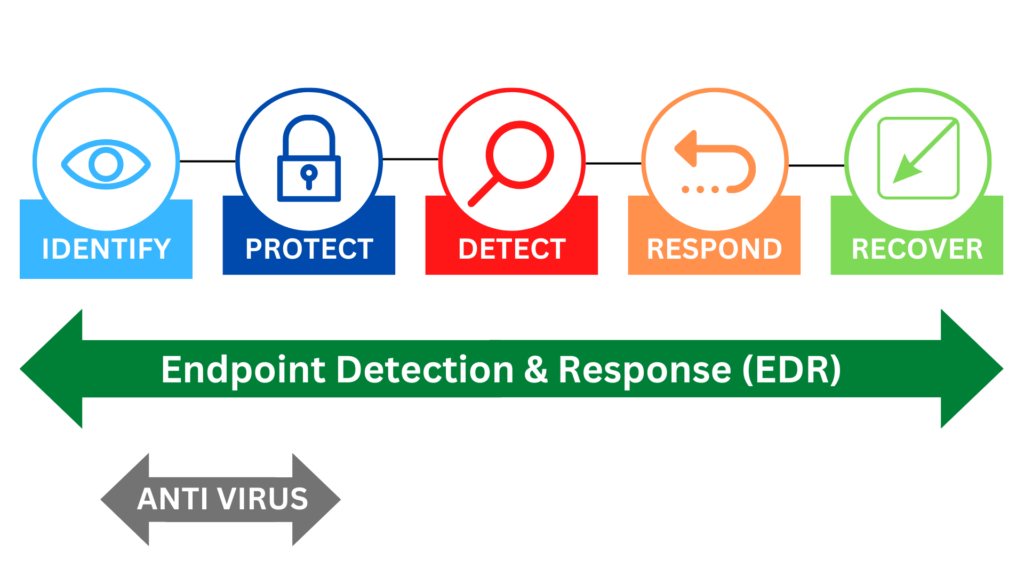
What Is EDR?
EDR stands for Endpoint Detection and Response. EDR is used to keep an eye out for unusual activity on system endpoints, including computers, phones, and servers, etc. The additional capabilities of an EDR include analytics, the context for the analytics, stopping potentially harmful behavior, and system correction or restoration. An EDR is often a system made up of components that carry out distinct security functions, as opposed to being one program or application.
Antivirus software, automated analysis and forensic software, endpoint monitoring and administration, and security team alert systems are a few examples of the components. With the aid of these technologies, an EDR can effectively stop incidents from happening, lessen immediate hazards, and promptly fix the problem after an incident.
What Is NDR?
NDR stands for Network Detection and Response. NDR’s main function is to keep an eye on network traffic, record any suspicious or malicious activity, and react to any risks that are found. Like EDR, NDR employs cutting-edge automated tools to stop cyber incidents, lessen present dangers, fix potential breaches, and alert the security staff of discoveries within the network. Machine learning is used by NDR, which can be virtual, on-premises, or cloud-based, to recognize both undiscovered and well-known network threats.
How Do NDR And EDR Interact?
We can see NDR as working to showcase visibility and transparency of traffic on a lateral level, whereas, EDR works to detect potential threats and malicious activity that may have been missed earlier on. An organization benefits from allowing both to be implemented so that the interaction reinforces and stabilizes efforts from multiple angles.
Ultimately, NDR analyzes packet data throughout the network traffic and effectively holds the flow together. EDR, as in the name, is the complementary monitoring system that monitors for endpoint attacks that normally go after computers and servers. If NDR is monitoring across the entire network – picking up and detecting wider attacks, then EDR is more focused (and perhaps less comprehensive than NDR) but still critical in preventing those pesky endpoint attacks.
The main point to recognize here is that you stand a better chance of monitoring and protecting your network traffic if you implement tools that serve specific functions, but also ones that work well when put together.
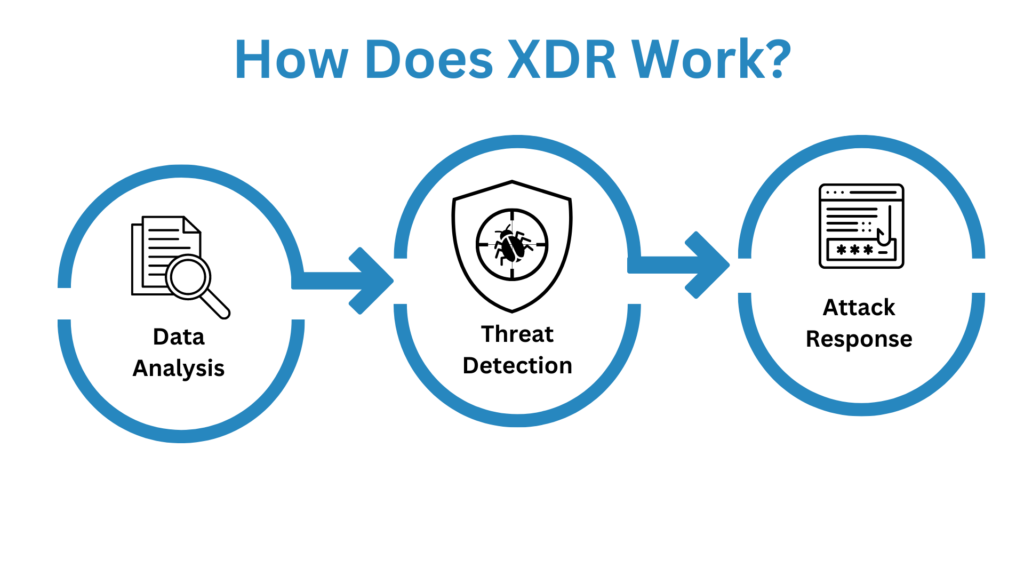
What Is XDR?
The idea of XDR was born out of the realization that the infrastructure of an organization cannot be viewed through a single lens in order to give the necessary coverage to reduce the threat surface. Endpoint, network, cloud, and employee-related compromises are all possible.
By combining detection and response capabilities for endpoints, networks, and cloud services in a single platform, XDR directly reacts to these restrictions. Because XDR is frequently provided as software-as-a-service (SaaS), enterprises can more efficiently utilize this technology.
The goal of XDR solutions is to provide organizations with relevant details and threat data so they can more effectively secure their data and operations in light of hybrid work environments, complicated IT architecture, and increasingly sophisticated threats.
Why Do You Need NDR And EDR?
Below are reasons to consider NDR and EDR including:
Why Your Business Needs EDR
Due to the frequent processing of private and secret information on their networks, businesses and organizations nowadays are even more vulnerable to various cyber threats. Next-generation technologies like advanced endpoint security systems can defend an organization’s IT infrastructure much more effectively than the majority of consumer antivirus configurations now on the market. The following are some of the main features and abilities of EDR:
Improved and Monitoring of Endpoint Security
Endpoint detection and response systems can give full monitoring and inspection of an organization’s numerous endpoints. Numerous endpoints to an organization’s security team by continuously collecting, analyzing, and processing data on a single interface. Instead of using several dashboards, EDRs give security specialists automatic access to real-time data through a single, centralized platform.
This enables them to quickly understand any detected security breaches and respond to cyber threats. The security staff of any company may investigate breaches much more quickly and easily, thanks to its powerful EDR component.
Additionally, regardless of where the endpoint device is physically located, your security team can respond to a security breach remotely if your company’s EDR system is cloud-based. Endpoint devices can instantly receive assistance from a security expert wherever they are and at any time.
Increased Cost-Efficiency
Businesses and organizations are frequently required to re-image an endpoint following infection using many traditional security methods. This entails wiping out all data and software from a device and reinstalling the operating system. As you may imagine, both the affected end user and the IT or network security staff may expend a great deal of time and energy throughout this procedure.
On the other hand, EDR can quickly and precisely identify the source of any infection or security breach and greatly reduce the requirement for re-imaging. In the case of a cyber breach, impacted users would seldom ever have to go through the process of reconfiguring their whole system or their equipment.
Automated Response & AI Learning
In today’s endpoint security market, automation is a game-changer. An EDR with strong automation capabilities can offer new levels of efficiency in proactive threat-hunting approaches that no standard antivirus can match. This will speed up its detection and response cycle.
An endpoint detection and response system (EDR) differs from earlier generations of antivirus tools in that it does not rely on a signature-based intrusion detection system. Instead, EDR uses AI and machine learning to create an anomaly-based threat detection search that can identify malicious behavior patterns and attacks through ongoing data analysis. The EDR system will immediately look into any suspicious activity across any endpoint in your network, react, and stop any attacks from successfully breaching an endpoint. This shields your environment against security holes that most conventional antivirus tools would typically fail to notice.
Greater Protection For Remote Work
Since Covid, there has been an even greater increase in the number of companies that have implemented remote or hybrid work arrangements that permit their employees to regularly work outside of their offices or places of business. Working from home offers flexibility and convenience, but it also leaves you more open to security breaches and cyberattacks. Most personal devices lack advanced endpoint security or intrusion prevention systems, making them more vulnerable to cyberattacks than in corporate environments where cybersecurity is continually monitored by an IT team.
Systems for endpoint detection and Response are the ideal answer to this challenge. A company’s IT or security team can now access, monitor, and defend every device on a corporate network with unparalleled simplicity, in contrast to earlier generations of endpoint security. With a cloud-based EDR system, security experts may quickly stop breaches from any place while remotely supporting any user’s technical needs.
What Is The Difference Between EDR And MDR?
Before we highlight the differences between EDR and MDR, it is important that we define what MDR is.
What Is MDR?
MDR stands for Managed Detection and Response. MDR is a service that employs humans to continuously watch, prioritize, and react to cybersecurity threats. By providing analysts with information and the tools to act on the endpoint, EDR systems enhance MDR. These can include gathering information to better prioritize threats, such as ensuring that running services, apps, users are logged in, local files, etc., or containment measures, such as setting up quarantines and shutting down services, etc.
MDR providers are able to provide posture hardening services and extend their threat coverage from network to endpoint detection and Response by leveraging the principles of network security monitoring combined with detection and prevention solutions, including EDR.
How MDR And EDR Interact
Although MDR and EDR are two distinct security solutions, they work together to close holes in security and resource availability. Simply put, MDR can benefit from EDR’s technologies to improve its capabilities for threat detection, analysis, and Response.
There isn’t really a competition of which is better when it comes to MDR vs. EDR. Yes, there is a difference between the two, but the majority of MDR providers use EDR functionality to get the greatest visibility possible throughout the entire environment, enabling rapid detection and proper response to threats and breaches.
EDR vs. MDR
EDR functions similarly to a security system, sounding an alarm if a window is smashed or a door is pushed open in an effort to deter the trespasser and notify the business owner of an issue. Sadly, even if the security system warns the business owner, he or she might not recognize an issue right away.
She has a business to manage, after all, and she is a busy woman. She is only one person, so if the break-in occurs when she is dozing off or attending a meeting, she might not see the alarm until after she has finished dozing off or the meeting has ended.
On the other hand, MDR is more like hiring a security guard: You already have an expert on-site, keeping an eye out for any suspicious activity. Should a break-in occur, the security guard can respond right away. That doesn’t mean that alarm systems aren’t useful, but they are more useful if you have a security guard keeping an eye on things as well.
NDR And EDR Solutions
The NDR and EDR solutions to consider are as follows:
NDR Solutions

WireX NDR Solution
Your security program’s overall maturity can be improved by incorporating NDR. It can be difficult to choose which platform provides the finest functionality with the most convenience. Introducing WireX Systems.
WireX Systems NDR is concentrating on the investigation to assist your team in moving from alerts and symptoms to diagnoses and remedies, whereas the majority of NDR suppliers are concentrating on the detection component to be the first to issue the alert.
How WireX NDR Solution Works
The robust platform from WireX Systems addresses important problems that are at the core of conventional network research. As previously stated, network security and visibility must focus on internal security threats and extend beyond the network’s perimeter (east-west traffic). However, there are two fundamental obstacles to effectively storing and analyzing mountains of packet data: complexity and Capacity.
Only a few days’ worth of payload data could ever be stored when saving information at the packet level (and the rest is high-level metadata). Since the industry statistics for how long it takes to detect a signal range between 120 days, by the time we would need to use those packets, they would have long since vanished.
The complexity of manipulating “bits and bytes” and turning them into knowledge presents the second difficulty. Even if you had the packets, it would be difficult to use them effectively because most packet-based systems are extremely difficult to handle and will need a network specialist and a security expert to operate them.
You are right if you think that this is too much for a human analyst to handle. In order to determine what actually occurred, they would need to be knowledgeable about each network protocol and be familiar with it from top to bottom.
WireX Systems’ main differentiators are exactly around these two challenges — WireX provides at least 180 days of payload information combined with an automatic analysis that does the heavy lifting for the analyst.
Comprehensive visibility, network analytics, and a deep understanding of the complex relationships in your network without sifting through vast amounts of data are what make WireX Systems Contextual CaptureTM technology invaluable. It removes the need for time-consuming and non-replicable processes like raw packet analysis.
A fully reconstructed OSI stack and months of in-depth network activity reveal relationships and interactions among network components that would otherwise remain hidden from the analyst. Threat intelligence from Contextual Capture enables you to move from alerts and symptoms to diagnostics and remediation by responding to threats with decisive context and even finding time to do proactive hunting.
Contextual capture has several advantages that go beyond providing adequate context for detection and Response. Traditional network detection tools are struggling to keep up with the massive amounts of data produced by analyzing network traffic, but WireX Systems’ NDR overcomes this problem with Big-Data Analytics, including high-performance databases, lightning-fast response times, and scalability to store many months’ worth of forensics history and intelligence. Your captured activities can be used to display, identify, track, and analyze network anomalies so that responses are prompt and focused. It is simpler to recognize and comprehend certain attack methods when the past and present are readily available.
Final Thoughts With WireX
Early warning signs of a potential attack or the initial stages of a breach can be detected with the WireX NDR solution. We can help you identify suspect remote access, download or delete specific files after doing a search for them on a file server, or launch a SQL transaction to extract records from a database in your zero trust architecture network.
Because of the high fidelity of our platform’s notifications, there are fewer false positives than with other systems, and we can order them according to severity. The automated response capabilities that save your team time and do away with manual response are the best features to ensure a completely safe zero trust acess (ZTA) network. Your security team doesn’t have to waste their time chasing ghosts through the network with WireX, and they can focus their efforts on real threats and proactive hunting.
Contact WireX Systems today to leap from chasing alerts and symptoms to having a clear context for diagnostics and remediation.






