The MITRE ATT&CK® framework is a tool created to increase cybersecurity knowledge by educating users about threats and attack vectors. It was developed and is kept up by the MITRE Corporation, a research and development facility funded by the US government (FFRDC).
The idea is that by understanding the myriad ways that attackers actually attack, organizations can better prepare for the risks.
The Enterprise Matrix, which lists potential attack vectors against an enterprise network, is the most well-known product of MITRE ATT&CK.
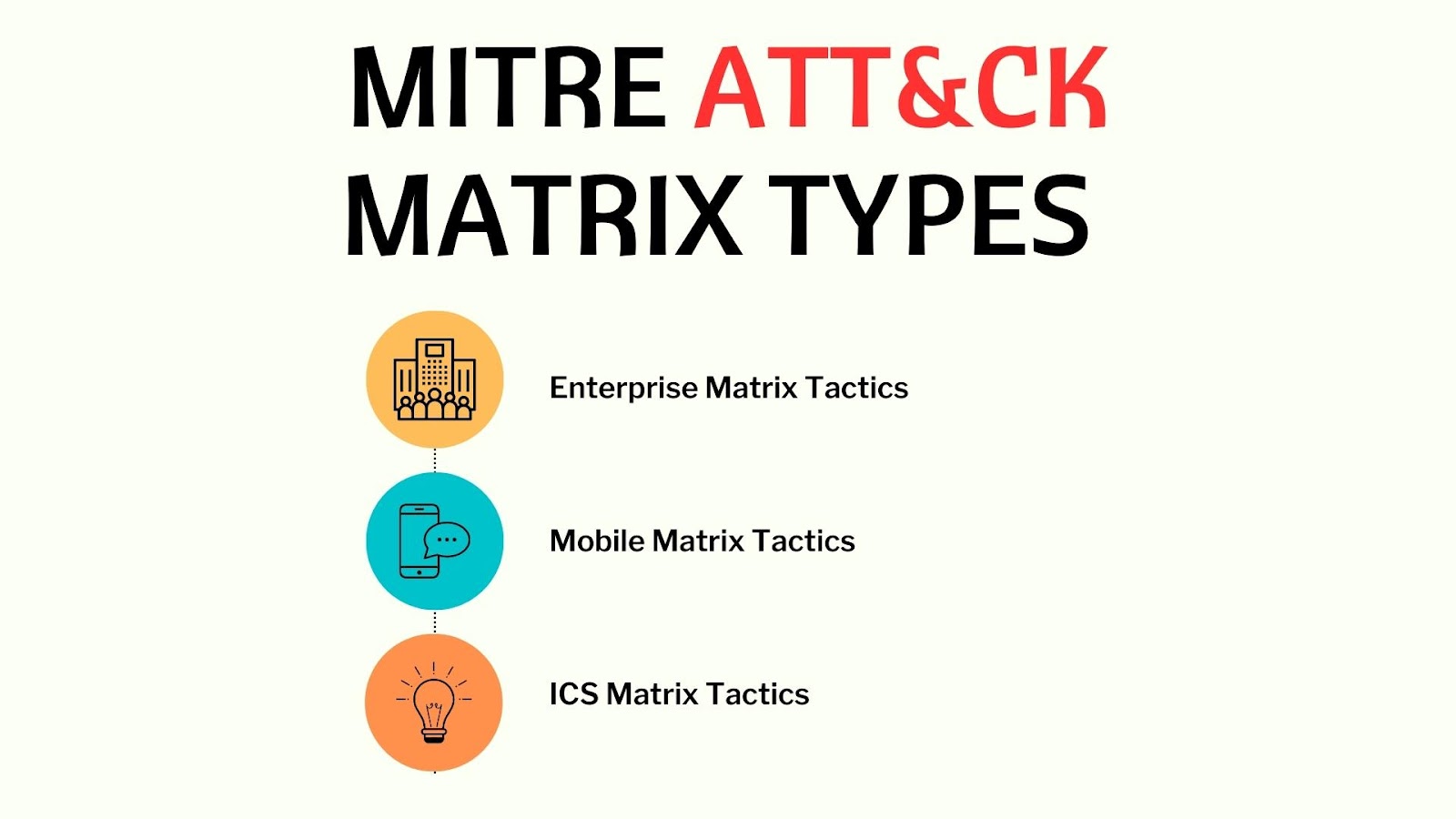
However, the MITRE ATT&CK framework includes four matrices in total. The framework also includes matrices outlining threats to mobile and ICS systems as well as a PRE-ATT&CK matrix that covers the pre-exploit phases of the cyberattack life cycle.
In this article, we will discuss what the MITRE ATT&CK Framework is, how it works, and how the framework can support your security initiatives.
What Is The MITRE ATT&CK Framework?
MITRE ATT&CK is an open framework for implementing cybersecurity detection and response programs. A global knowledge base of adversarial tactics, techniques, and procedures (TTPs) based on in-the-field observations is included in the free-to-use ATT&CK framework. Assisting IT, security, and compliance organizations in effectively identifying security gaps, assessing risks, and removing vulnerabilities, ATT&CK imitates the actions of actual attackers.
Penetration testers, red and blue teams, security solution providers, threat intelligence vendors, etc., can all communicate using the same language, thanks to ATT&CK’s common taxonomy. The Groups database in ATT&CK also keeps tabs on the global activities of cybercriminal gangs and threat actors.
History and Evolution Of MITRE ATT&CK
Researchers at the MITRE Corporation started cataloging the various techniques threat actors employ to break into networks and launch attacks in 2013.
The ATT&CK framework was community-driven from the start and was introduced as a wiki. The original version contained nine tactics, three of which—Privilege Escalation, Lateral Movement, and Exfiltration—were first introduced in Lockheed Martin’s Cyber Kill Chain. Sections on detections and mitigations were present right away.
Since then, MITRE has discovered thousands of distinct methods that adversaries employ to carry out cyberattacks.
These methods are compiled into a set of tactics by ATT&CK to aid security practitioners in quickly identifying, isolating, and eliminating threats. The techniques describe the steps the adversary takes to accomplish their objectives, while the tactics describe what the adversary is attempting to do (for example, steal credentials) (e.g., brute force methods).
Cyber Kill Chain Vs. MITRE ATT&CK
MITRE ATT&CK™ and the Cyber Kill Chain™ are frameworks to address cyberattacks against an organization. While the Cyber Kill Chain’s seven phases provide a high-level overview of the cyberattack process, MITRE ATT&CK offers a broader range of information about cyberattacks, including specifics like attack methods and procedures and links to industry advisories.
What Is the Cyber Kill Chain?
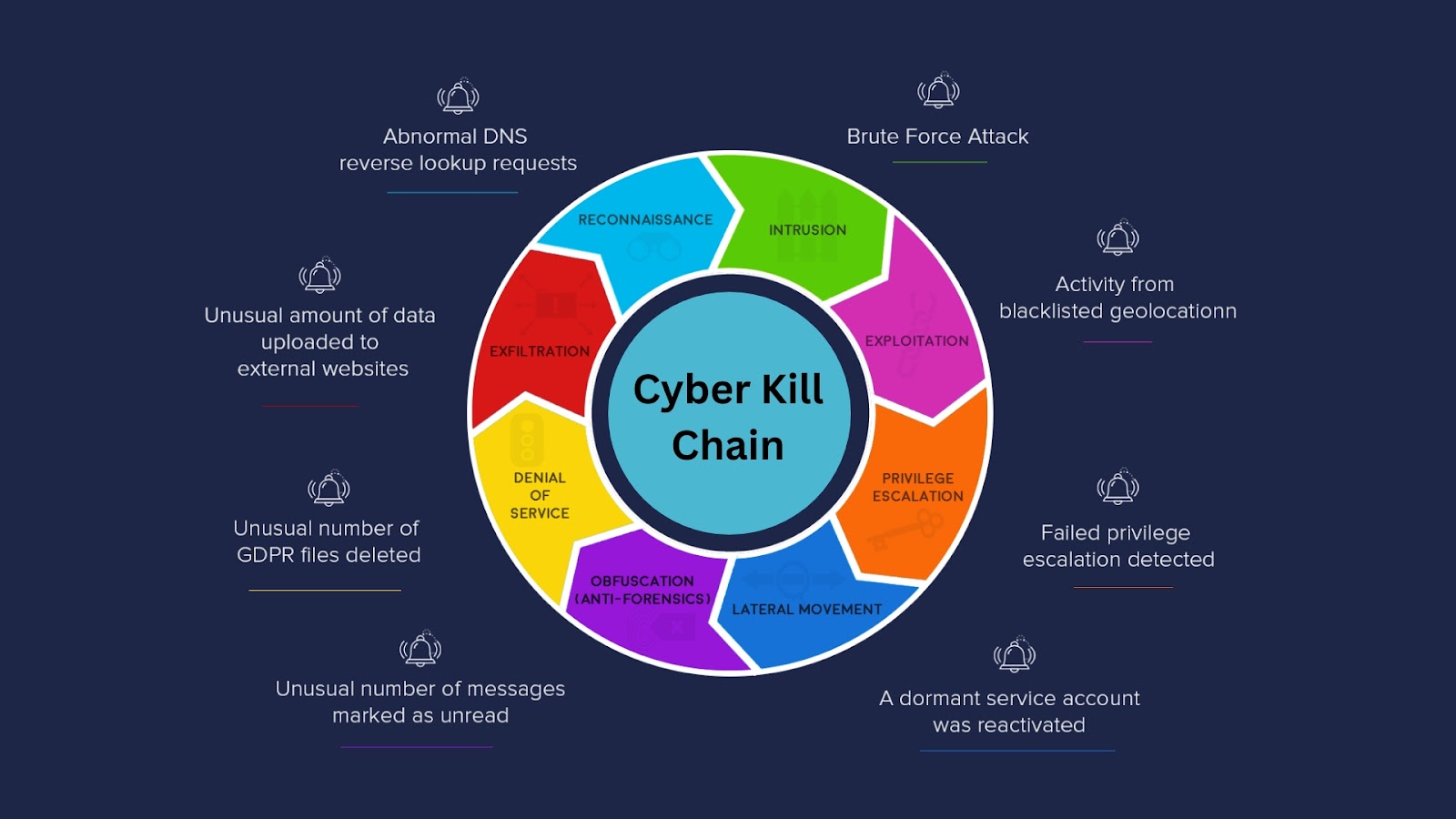
The Cyber Kill Chain is a cyberattack framework developed by Lockheed Martin and released in 2011. The phrase “Kill Chain” was borrowed from a traditional military concept that refers to the process of organizing and launching an assault.
The Cyber Kill Chain divides all cyberattack behaviors into sequential tactics, from reconnaissance to achieving goals, much like MITRE ATT&CK does. Additionally, the Cyber Kill Chain promotes the idea that every stage of the attack presents a chance to thwart it by “breaking the kill chain.” According to Cyber Kill Chain, a thorough defensive strategy will result from the planning and testing of security controls for each identified stage of an attack.
How MITRE ATT&CK Differs from Cyber Kill Chain
The Cyber Kill Chain claims that all cyberattacks must use a particular order of attack tactics in order to be successful, whereas MITRE ATT&CK does not make this claim. A basic series of steps that make up a cyberattack is known as the “Cyber Kill Chain,” and it is combined with the defensive security axiom that “breaking” any stage of the “kill chain” will prevent an attacker from successfully achieving their objective.
MITRE ATT&CK is more than alist of attack strategies. It is a comprehensive knowledge base that links cybersecurity knowledge specific to a given environment along a hierarchy of tactics, techniques, procedures, and other common knowledge, including the attribution of particular adversarial groups.
Who Uses MITRE ATT&CK?
ATT&CK is a free tool that private and public sector organizations of all sizes and industries have widely adopted. Users include internal teams interested in developing secure systems, applications, and services, as well as security defenders, penetration testers, red teams, and cyber threat intelligence teams. Organizations can assess whether they are gathering the appropriate data to effectively detect attacks and gauge how well their current defenses are performing by looking at the wealth of attack (and attacker) information it contains.
ATT&CK deliberately adopts an attacker’s point of view in contrast to other models written from a defender’s perspective to aid organizations in comprehending how adversaries approach, plan, and successfully carry out attacks. This makes ATT&CK a fantastic resource and teaching tool for people interested in a career in cybersecurity or threat intelligence as well as for those who just want to learn more about the tactics used by attackers.
How The MITRE ATT&CK Framework Works
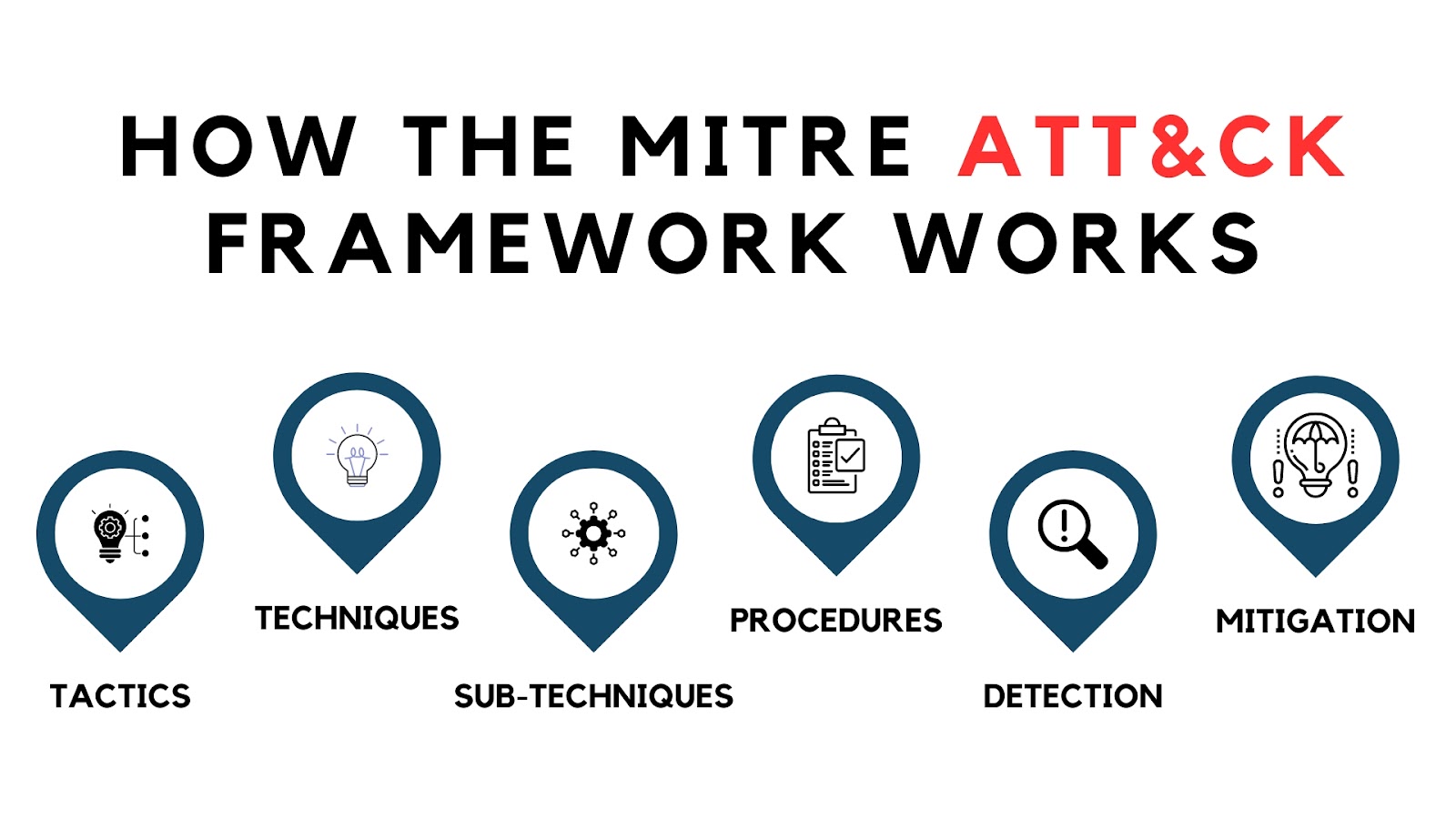
The MITRE ATT&CK framework aims to increase knowledge and comprehension of how cyberattacks operate. It creates a hierarchy out of the information to achieve this, including:
Tactics: ATT&CK MITRE High-level goals are tactics that an attacker may want to accomplish during a cyberattack. The various phases of an attack, such as gaining initial access to a system, compromising user accounts, and moving laterally through the network, are included.
Techniques: MITRE ATT&CK defines a number of Techniques for carrying out each of the high-level Tactics. For instance, a hacker may use a brute force attack to guess user credentials, or they may be taken directly from the operating system.
Sub-Techniques: There are numerous additional ways to implement some MITRE ATT&CK Techniques (called Sub-Techniques). For instance, a credential stuffing attack or cracking password hashes could be used to carry out a brute-force password attack.
The Tactics, Techniques, and Sub-Techniques in MITRE ATT&CK drill down to a particular means by which an attacker may accomplish a target.
For each of these methods, MITRE ATT&CK provides the following information in addition to a description of the attack:
Procedures: Procedures give specific instructions on how to apply a technique. This includes malware, hacking instruments, and threat actors who are known to employ that specific tactic.
Detection: For a specific technique, MITRE ATT&CK suggests approaches to its detection. This section outlines the kinds of data that must be gathered to detect a specific attack, which is invaluable for designing cybersecurity defenses.
Mitigation: The mitigation section outlines actions a company can take to avoid or lessen the effects of a specific technique. Multi-factor authentication (MFA), for instance, is typical mitigation for methods intended to gain access to user accounts.
MITRE ATT&CK Matrix Types
Enterprise Matrix Tactics
An adversary model and framework for describing the steps an adversary might take to infiltrate and operate within an enterprise network is called ATT&CK for Enterprise. With the help of the model, post-compromise adversary behavior can be better understood and described.
By describing the tactics, techniques, and procedures (TTPs) cyber adversaries use to gain access and carry out their objectives while operating inside a network, it both broadens the knowledge of network defenders and helps with prioritizing network defense.
Mobile Matrix Tactics
The MITRE ATT&CK mobile matrix employs the same eleven tactics as the enterprise matrix and is created to cover the same phases of the cyberattack life cycle. The mobile matrix, in contrast to the enterprise matrix, which focuses on enterprise networks, focuses on threats and attack vectors particular to mobile devices.
Thus, compared to the enterprise matrix, the mobile matrix has a very different set of techniques and sub-techniques. More general attack vectors that also apply to mobile devices are not included because these techniques are concentrated on mobile-specific attack vectors.
There are 100 mobile techniques in total, but the sub-techniques category that was introduced with the enterprise matrix has not yet been added to this matrix.
ICS Matrix Tactics
ATT&CK for ICS includes the ATT&CK for Enterprise techniques that can be leveraged by an adversary in the final stages of either a targeted or untargeted attack against an industrial process. Although the Enterprise and ICS technology domains have a lot in common, ATT&CK for ICS is primarily concerned with the attacks that enemies mount against ICS’s non-IT-based systems and functions.
Its goal is to identify and define differences in ICS environments, from tactics and procedures to technology and resources that are specific to a given domain. Industry verticals (Electric, Oil and Gas, Manufacturing) have distinctive characteristics even within ICS.
Since ATT&CK for ICS is vertically independent, it can be used with ICS systems that support a variety of industrial processes. The ICS-specific assets perform a consistent function regardless of the underlying operating system, hardware platform, or application in ICS networks, which are highly heterogeneous environments.
Leveraging MITRE ATT&CK For Cyber Defense
The MITRE ATT&CK framework is intended to be a tool, not just a knowledge base. The MITRE ATT&CK matrix can be operationalized by security operation center (SOC) teams in a number of ways, including:
Designing Defenses: The MITRE ATT&Ck framework describes techniques for identifying and countering various cyberattack methods. This information can be used to check that a company has the necessary defenses in place and is gathering the data needed to identify a particular threat. The methods that an organization prioritizes can be determined by threat intelligence.
Incident Detection: The MITRE ATT&CK framework outlines the methods for identifying a specific threat. This information helps the security team to determine the next-generation firewall (NGFW), security information and event management (SIEM) solution, and other security solutions should use this data to create detection rules.
Incident investigation: The MITRE ATT&CK framework explains an attack’s methodology and the malware that employs specific tactics. Because it enables an investigator to recognize the MITRE ATT&CK Technique being used and make use of the additional data provided by the framework, this information is crucial for incident investigation.
Remediation of Infection: The MITRE ATT&CK framework outlines a specific technique’s operation as well as the capabilities of various malware samples and threat actors. Since it describes the actions that an attacker has taken and that must be undone to remove the infection, this can aid in remediation efforts.
Reporting: The MITRE ATT&CK framework streamlines reporting by standardizing terminology. Tools and analysts can produce reports referencing specific framework techniques, which provide more detail and potential mitigation steps.
Threat Hunting: MITRE ATT&CK’s descriptions and detection data are very helpful for threat hunting. Threat hunters can determine if they have been targeted by attackers using a specific technique and whether or not existing security solutions are able to detect and prevent these attacks by conducting a MITRE ATT&CK evaluation and working through each of the techniques described in the framework.
Final Thoughts
The MITRE ATT&CK framework is a useful resource for enhancing understanding and communication about cyberattacks. WireX solution has integrated MITRE ATT&CK’s taxonomy into its entire solution portfolio to improve incident response. The descriptions of malware capabilities and forensic reports both include mappings to MITRE ATT&CK techniques.
This offers several benefits to a SOC analyst. The use of MITRE ATT&CK makes it simple to comprehend the root causes, attack flow, and the attacker’s intent at each stage when analyzing a specific attack. A SOC team can quickly comprehend the scope of an attack, any necessary remediation, and how to improve defenses for the future by comprehending what the attacker is attempting to accomplish and how.
WireX’s solution makes cyberattacks more transparent and understandable by integrating MITRE ATT&CK. Reach out to us to learn more about how WireX and MITRE ATT&CK can streamline and improve incident detection and response.
FAQ
What are the differences between sub-techniques and procedures?
Sub-techniques and procedures describe different things in ATT&CK. Procedures are used to describe how techniques are used in the wild, while sub-techniques are used to categorize behavior.
Furthermore, since procedures are particular applications of techniques and sub-techniques, their execution may involve a number of additional behaviors. For instance, a procedure implementation containing several (sub)techniques covering the PowerShell, Process Injection, and Credential Dumping against LSASS behaviors shows an adversary using PowerShell to inject into lsass.exe to dump credentials by scraping LSASS memory on a victim.
What technologies does ATT&CK apply to?
Windows, macOS, Linux, Network infrastructure devices, Container technologies, Office 365, Azure Active Directory, and Google Workspace, are all examples of enterprise IT systems. Cloud systems include Infrastructure-as-a-Service (IaaS), Software-as-a-Service (SaaS), and Infrastructure-as-a-Service (SaaS) as well. Mobile devices include Android and iOS.






