Professionals in cyber security are always on the lookout for security lapses that could jeopardize the availability, confidentiality, and integrity of their organization’s information assets. However, the harsh truth is that these occurrences are unavoidable; security incidents will still happen despite the precautions taken.
To ensure that organizations can recover from an attack or other security event and prevent potential business operations disruption, it is essential to have a strong incident response plan, which provides instructions on what to do in the event of a security incident.
In this article, we will look at what an incident response plan is, who in an organization is responsible for it, the steps taken for incident response, and how to develop an incident response plan.
What Is An Incident Response Plan?
An incident response plan is a set of procedures and processes that allow organizations to identify, contain, and eliminate cyber threats and recover from incidents. It must be created in advance of an incident and should be a crucial part of any organization’s cyber security strategy.
Detailed procedures for locating, responding to, and recovering from a security incident should be included in an incident response plan. Along with the resources, tools, and procedures required to properly respond to an incident, it should also outline the duties and responsibilities of the incident response team.
The response plan should also include a communication plan to ensure that all stakeholders are informed about the incident, as well as a detailed post-incident analysis process to identify areas for improvement. Having a plan in place will clarify roles and responsibilities and increase the chances of success in responding to an incident.
What Is The Difference Between An Incident Response Plan And Business Continuity Plan?
The difference between an incident response plan and a business continuity plan lies in their purpose and scope. A business continuity plan is created to assist organizations in continuing to operate both during and after a disruption, whereas an incident response plan is created to assist organizations in responding to defending against and recovering from security incidents.
An incident response plan is focused on identifying, containing, and eliminating cyber threats and recovering from incidents. It is a set of guidelines that a company adheres to when handling a security incident. In addition to steps for recovering from the incident, it should include steps for locating, containing, and eliminating the threat.
A business continuity plan, on the other hand, is focused on ensuring that the organization can continue to operate during and after a disruption. It should include the steps needed to maintain or restore operations, such as the steps to back up data and systems, as well as steps to ensure the continuity of essential services and personnel.
A business continuity plan aims to guarantee that the organization can continue to function both during and after a disruption. It should outline the procedures required to maintain or resume operations, such as how to back up data and computer systems and how to make sure that key employees can work and services continue to be provided.
Who Is Responsible For Incident Response Planning?
The cybersecurity team of the organization is in charge of planning the incident response process. The security team is responsible for spotting potential threats, creating policies, assembling a response team, and instructing staff.
The incident response plan should be thorough and current, so the security team should collaborate closely with other departments like IT, legal, and HR, executive management from the C-Suite. Planning an incident response effectively requires this level of cooperation.
Why Is An Incident Response Plan Important?
An incident response plan is an essential part of any organization’s cybersecurity strategy. It outlines the steps that should be taken in the event of a security incident and helps ensure that the organization is prepared to respond quickly and effectively. A well-crafted incident response plan can help minimize the impact of a security breach, reduce the amount of disruption to operations, and protect the organization’s reputation.
The importance of an incident response plan cannot be overstated. Without a plan in place, organizations are more likely to experience data breaches, business disruptions, and reputational damage. An incident response plan helps organizations identify, contain, and eliminate cyber threats and recover from incidents. It also clarifies roles and responsibilities, which increases the chances of success in the event of a security incident.
An incident response plan should include a detailed list of procedures for responding to incidents, including:
- Establishing the incident response team and assigning roles and responsibilities.
- Developing communication protocols for the incident response team.
- Creating a process for identifying and responding to incidents.
- Putting in place procedures for documenting and reporting incidents.
- Creating policies for containing and mitigating incidents.
- Setting up processes for recovering from incidents.
- Establishing procedures for reviewing and updating the incident response plan.
What Are The Different Types Of Security Incidents?
Security incidents can take many forms and can vary in severity. It is important to understand the different types of incidents that can occur so that you can properly prepare and respond to them.
Web Application Attack
One of the most common and dangerous security incidents that organizations encounter today is web application attacks. These assaults can be used to access private data, stop services, or even inflict financial harm.
An attack against a website or web application is referred to as a web application attack. These attacks are typically carried out by taking advantage of holes in the web server or application code. Any number of attack methods, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and remote file inclusion, can be used by attackers to access the application (RFI).
Phishing Attack
Phishing is one of the most common types of security incidents, and it involves attackers sending malicious emails or other messages in an attempt to gain access to sensitive information or systems. These messages can appear to be from legitimate sources, such as a bank or other financial institution, and they often contain links or attachments that can lead to malicious software being installed on the recipient’s computer.
The goal of a phishing attack is to steal sensitive information such as usernames, passwords, credit card numbers, and other valuable data. It is important to be aware of the signs of a phishing attack, as they can be difficult to detect. Some signs to look out for include:
- Emails that contain links or attachments that look suspicious
- Requests for personal information such as usernames, passwords, or credit card numbers
- Emails that contain spelling or grammatical errors
- Emails that appear to be from a legitimate source, but the email address does not match the sender
- Emails with a sense of urgency or pressure to act quickly

Privilege Escalation Attack
By taking advantage of flaws in the system’s security controls, a malicious actor tries to gain unauthorized access to systems or data in a cyberattack known as a privilege escalation attack. These attacks can happen when a user has access to a system or application that they shouldn’t have or when a user has been given privileges that go beyond what is required for them to perform their job duties.
A privilege escalation attack can be accomplished by taking advantage of well-known flaws in the software or system, as well as by using subpar passwords or other authentication methods. Once inside, the attacker can take advantage of the elevated privileges to access more sensitive information or carry out malicious deeds.
Insider Threat
Any organization should be extremely concerned about insider threats. They originate from insiders, in other words legitimate users, who are intent on malicious behavior, such as resentful workers, or they could even be careless or negligent workers. Insider threats can seriously harm an organization’s systems and data and are challenging to identify.
Any action taken by a worker, contractor, or another person with access to a company’s systems and data that could be harmful to the company is considered an insider threat. Insider threats may be purposeful or accidental. Insider threats that are malicious in nature involve threat actors who have gained access to a company’s systems, such as rogue employees or hackers. Employees who are careless or negligent and who may not be aware of the risks involved in their actions frequently pose unintentional insider threats.
DoS Attack (Denial-Of-Service Attack)
A denial-of-service (DoS) attack is a type of cyberattack that tries to prevent its intended users from using a computer or network resource by overloading the target with unwarranted requests or data or by taking advantage of flaws in the system. DoS attacks are typically carried out by bad actors who want to disrupt services or deny access to particular websites or resources.
DoS attacks can be launched in a variety of ways. The most frequent kind of attack is a Distributed Denial-of-Service (DDoS) attack, which makes use of numerous computers or other devices to bombard the target with a lot of traffic. Given that the attacker can generate the traffic using hundreds or even thousands of computers, this type of attack is particularly challenging to defend against. Application-level attacks, which target a specific application or service, and protocol-level attacks, which target the underlying network protocol, are additional types of denial-of-service attacks.
Malware Attack
One of the most common types of security incidents is malware attacks, which can be extremely damaging to an organization. Malware is computer software that is intentionally designed to access a network or computer system without authorization. It can be used to steal data, interfere with business processes, or even harm real property.
Malware can spread via email, malicious websites, or by taking advantage of flaws in software. Additionally, it may be installed on a user’s computer covertly. Malware can be used to spy on users, steal data, or start distributed denial-of-service (DDoS) attacks after it has been installed.
Organizations should be aware of the various forms of malware and how to safeguard their systems against these dangers. Malware commonly comes in the form of viruses, worms, Trojan horses, rootkits, and ransomware.
Steps Of Incident Response
The following are the steps of incident response:
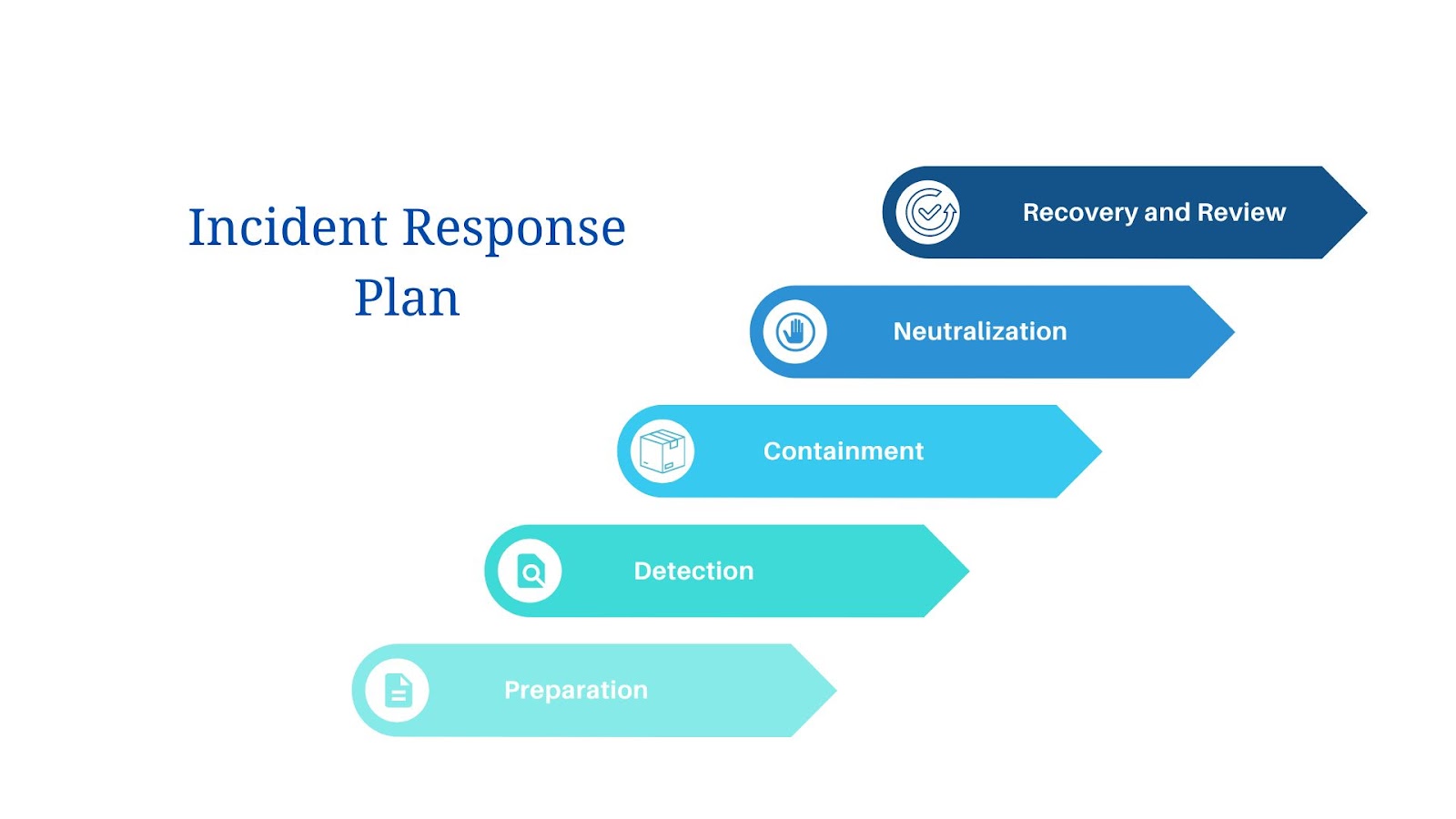
Preparation
The first step in developing a successful incident response plan is preparation. It entails preparing for potential security incidents in advance and anticipating them. If an incident does happen, this enables organizations to respond quickly and effectively.
Organizations should identify potential risks and vulnerabilities, develop incident response protocols, and establish a response team when getting ready for an incident. Assessing the organization’s systems and data for any flaws that attackers could exploit is necessary to identify potential risks and vulnerabilities.
Threats like malicious software, phishing scams, and insider threats should be considered in both the internal and external portions of this assessment.
Detection
In order to reduce damage and stop further incidents, detection aims to identify any potential security incidents as soon as possible. Depending on the size of the organization and the complexity of the security incident, detection can be either manual or automated.
Security analysts and other personnel with the necessary training to identify and look into suspicious activity typically perform manual detection. This entails keeping an eye on networks and systems for any unusual activity, including unusual data transfers and logins, as well as keeping an eye out for malicious traffic and unauthorized access attempts.
Security tools like intrusion detection systems (IDS), antivirus software, and other security software are used for automated detection. These instruments are made to identify suspicious activity and notify security personnel. Automated detection can be used to identify both known and unidentified threats, as well as to identify malicious activity as soon as it takes place.
Containment
Any incident response plan must include containment. By isolating the affected systems and stopping the spread of malicious activity, it is the process of limiting the harm caused by an attack or incident. The incident response process has two steps: detection and containment.
Containment strategies can be divided into two categories: technical and non-technical. Technical containment measures aim to stop the spread of malicious activity by using technical tools and techniques like firewalls, intrusion detection systems, and antivirus software.
Non-technical containment measures entail taking actions like cutting off access to user accounts and network services, along with isolating the affected systems from the rest of the network.
Neutralization
Neutralization is the process of eliminating the threat posed by a security incident. It entails locating the attack’s origin, putting an end to the attack, and quarantining any damaged systems or data. It’s crucial to understand that neutralization does not always imply that the attacker has been identified—in some cases, this may not even be possible.
The first step in neutralizing an attack is to identify the source of the attack. To identify the source of the attack, this can be done by examining logs, tracking network traffic, and other pieces of evidence. The attack must be stopped after the source has been located. The IP address of the attacker’s source can be blocked, their account can be disabled, or other steps can be taken to stop the attack from continuing.
Recovery
Recovery is the final step of the incident response process and involves restoring the affected systems to their pre-incident state. This is often the most challenging and time-consuming part of the incident response process. The goal of the recovery phase is to return the system to its original state, while also taking measures to prevent the incident from occurring again in the future.
The first step in the recovery phase is to identify and remove any malicious code or malware that may have been used to compromise the system. Running antivirus scans and removing any leftover malicious code may both be required for this. Since malicious code has the potential to persist in doing harm even after the incident has been dealt with, it is crucial to make sure that it is all eliminated from the system.
Once the malicious code has been removed, the system must be restored to its pre-incident state. This may involve restoring data from backups, reinstalling applications, and reconfiguring system settings. The restoration of all the data and applications that were available before the incident is crucial.
Review
The final step of an incident response plan is review, which is essential to the procedure. The review’s objectives are to assess the incident response plan’s effectiveness and pinpoint areas for development. Due to the dynamic nature of the threat environment and the constant emergence of new threats, it is crucial to regularly review the incident response plan.
The review should involve analyzing the incident from start to finish, including the detection, containment, and recovery phases. A performance evaluation of the response team and any necessary adjustments to the incident response plan should also be included. It’s also critical to think about any fresh threats that have surfaced since the previous review and how the incident response plan might need to be revised to address them.
What Are Incident Response Services?
Incident response services are a set of procedures that help organizations identify, contain, and eliminate cyber threats and recover from incidents. These services are created to quickly detect and respond to security incidents and are specifically tailored to the needs of the organization.
When an incident happens, the incident response team is in charge of locating the problem, judging the incident’s gravity, and taking the necessary actions to contain, mitigate, and remedy the problem. Services for incident response are created to assist organizations in recognizing, containing, and removing threats as well as recovering from incidents.
Organizations should look for a provider that offers a full range of services when choosing an incident response service provider. These services ought to cover incident assessment and analysis, planning, and execution of the incident response, recovery from the incident response, and post-incident review.
Additionally, the incident response service provider should be technically qualified and experienced to deliver the services that the organization needs. A wide variety of security incidents, including malware, phishing, privilege escalation, insider threats, and DoS attacks, can be analyzed and investigated in this way.
How To Develop An Incident Response Plan
Having an incident response plan is essential for any organization, regardless of size. It helps to protect the organization from cyber threats, reduce the impact of cyber incidents, and increase the chances of a successful recovery. But how do you develop an incident response plan? Here are some steps to help you get started.
Identify Potential Risks
Identifying potential risks is an important first step in developing an incident response plan. It necessitates knowledge of the organization’s resources, weaknesses, and threats. Analyzing the organization’s current security measures, spotting any security holes, and figuring out which threats could exploit those holes are all part of this process.
To find potential risks, organizations should use a risk assessment process. The organization’s assets should be identified, their value should be understood, and the likelihood and effects of various threats should be evaluated during this process. The risks should then be ranked in order of importance by the organization.
Establish Procedures
Establishing procedures is an essential part of creating an incident response plan. It is important to have a clear understanding of the steps that need to be taken in the event of an incident. The procedures should be tailored to the particular organization and should include identification of the incident, containment, analysis of the situation, recovery, reporting, and prevention.
Set Up A Response Team
Setting up a response team is an integral part of creating an incident response plan. To assist in locating, containing, and getting rid of cyber threats, it is crucial to have a team of people with the appropriate expertise.
People from a variety of departments, including IT, security, legal, and human resources and management, should make up the response team. In the event of a security incident, the team will be able to make decisions and take action with the assistance of each department’s expertise. It is important to note that the response team should not be limited to the IT department.
Train Your Response Team And Staff
Without proper training, your team may not know how to respond effectively and quickly to an incident, leading to further damage and disruption.
Define and record the roles and responsibilities of each person before beginning to train your response team and staff. The specific duties and procedures that each team member is in charge of in the event of an incident should also be included. By doing this, you can make sure that everyone understands their responsibilities and is prepared to respond appropriately in the event of an incident.
The instruction on the incident response plan itself comes next. This should contain a summary of the strategy as well as specific instructions on how to handle various incident types. Any tools or technologies that might be used in the response process should be covered in this training as well.
Achieving Greater Threat Coverage And Response With NDR
Cybersecurity is getting tougher, and companies are scrambling to equip themselves with everything they can to stay protected. This has become especially relevant as tech possibilities are widening in the coming years. For example, Cloud Computing, 5G, Metaverse, and Electric Vehicles are considered to be top tech areas for 2023. And this means heightened attention to potential blind spots.
However, NDR is a vital part of this equipment as it provides coverage and protection for all network traffic coming in and going out of your system. Furthermore, NDR fills in for all the blind spots present in previous security solutions and provides extremely useful threat intelligence to help you stay on top of attacks.
Getting Started With WireX Systems
At WireX Systems, we understand your pain when it comes to properly investigating every alert. And currently, the investigation tools that are presently available have failed to meet enterprise business needs. However, with our approach, we deliver comprehensive security intelligence in actual human-readable format, so you can save effort and time when validating alerts and responding to security incidents.
You can learn more about how our technology reduces breach dwell time, but we also have a Whitepaper on the top 3 requirements to turbocharge your incident response.
And, as always, reach out to us, and we’ll discuss how to best support your network security needs!







