With the recent DigiCert revocation incident¹, that caused major disruption to customers’ workflows all due to a quality assurance failure on DigiCert’s part, it is even more evident how important complete network visibility is to enterprises. While we all recognize how important the pedigree of trust is with a partner, the cost (and risk) associated with a partner’s error, highlights just how critical validation, testing and complete network visibility is to ensure continuous uptime for customers.
Let’s take a closer look at how WireX Systems Ne2ition Platform was used to quickly detect and utilize historical data to find the root cause of the issue. Watch the webinar below >>
Because WireX Systems records the entire stream of network traffic, it is passively monitoring the network behavior and indexing payload activity at all times. In the case of DigiCert, an analyst would open the investigation screen in the Ne2ition platform and open a new case. Having complete historical context of the network intelligence enables rapid access and resolution of situations like the DigiCert situation.
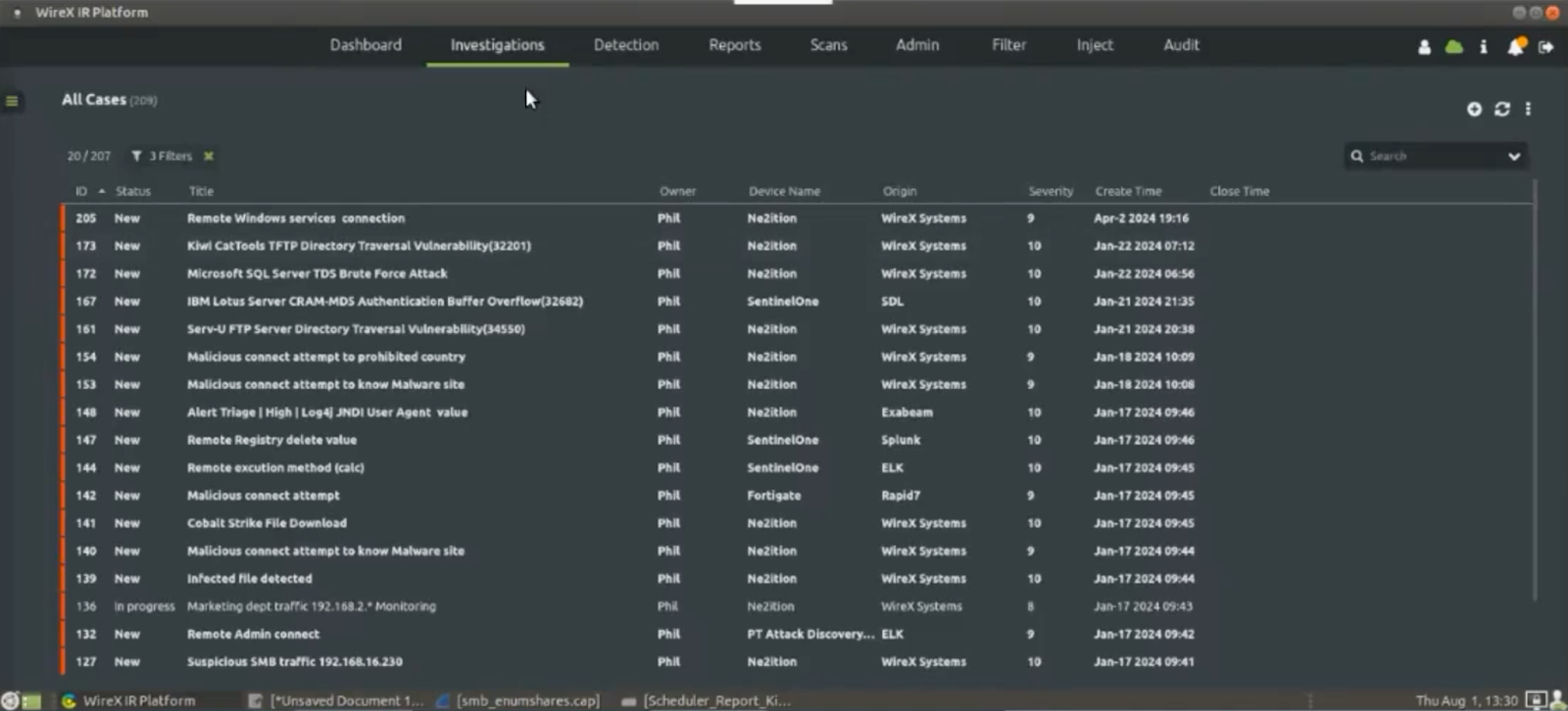
The agent would start completely from scratch. The best approach is to divide up the network and start with small chunks of data perhaps starting with an entire subnet.
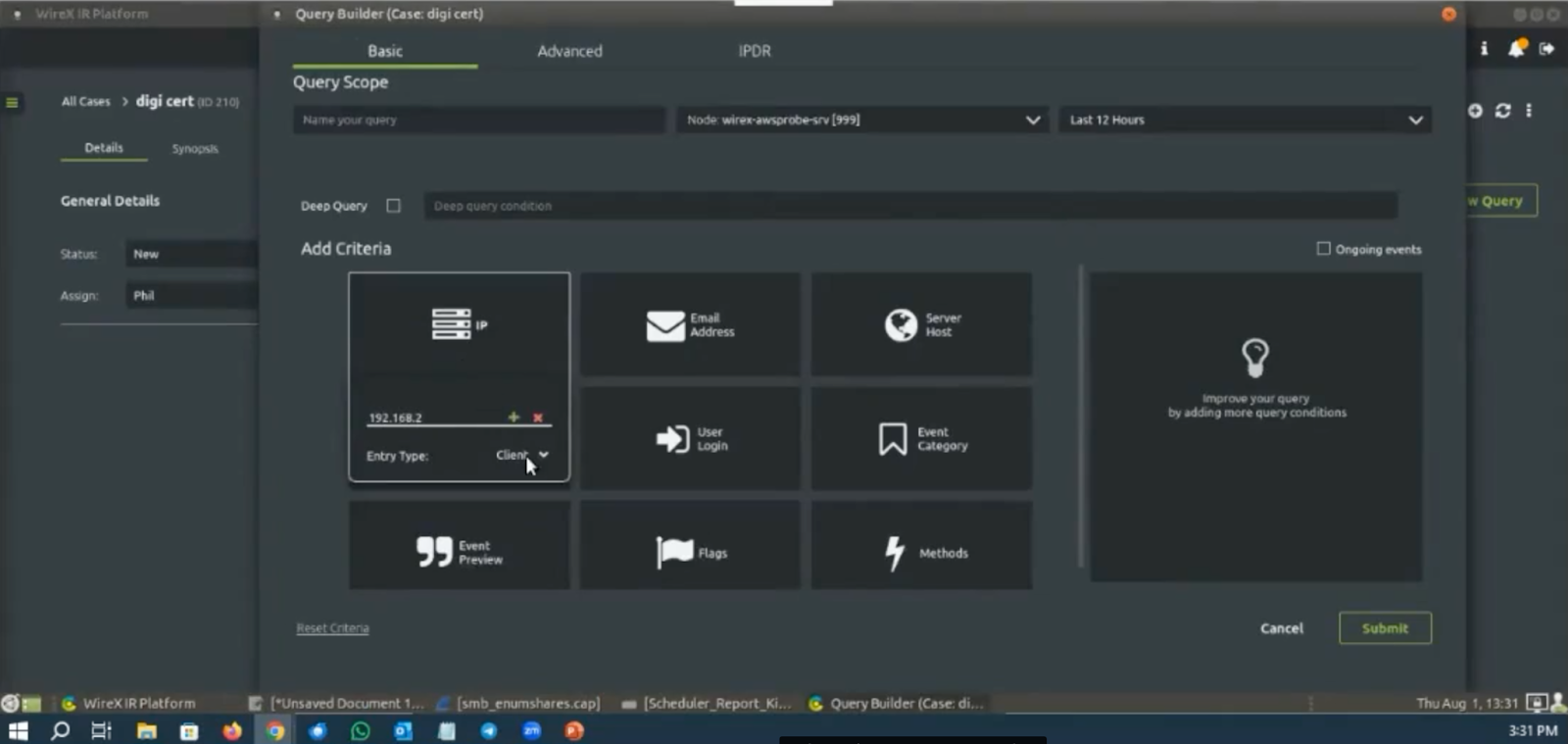
In this case, the agent starts with the marketing department using a partial IP and appropriate time range. From here, the operator can see a lot of database activity, a lot of http and network-level requests, but what they really want to see is what certificates moved during this timeframe. So utilizing this same segment of the marketing department, the agent would simply choose Events > Certificates.
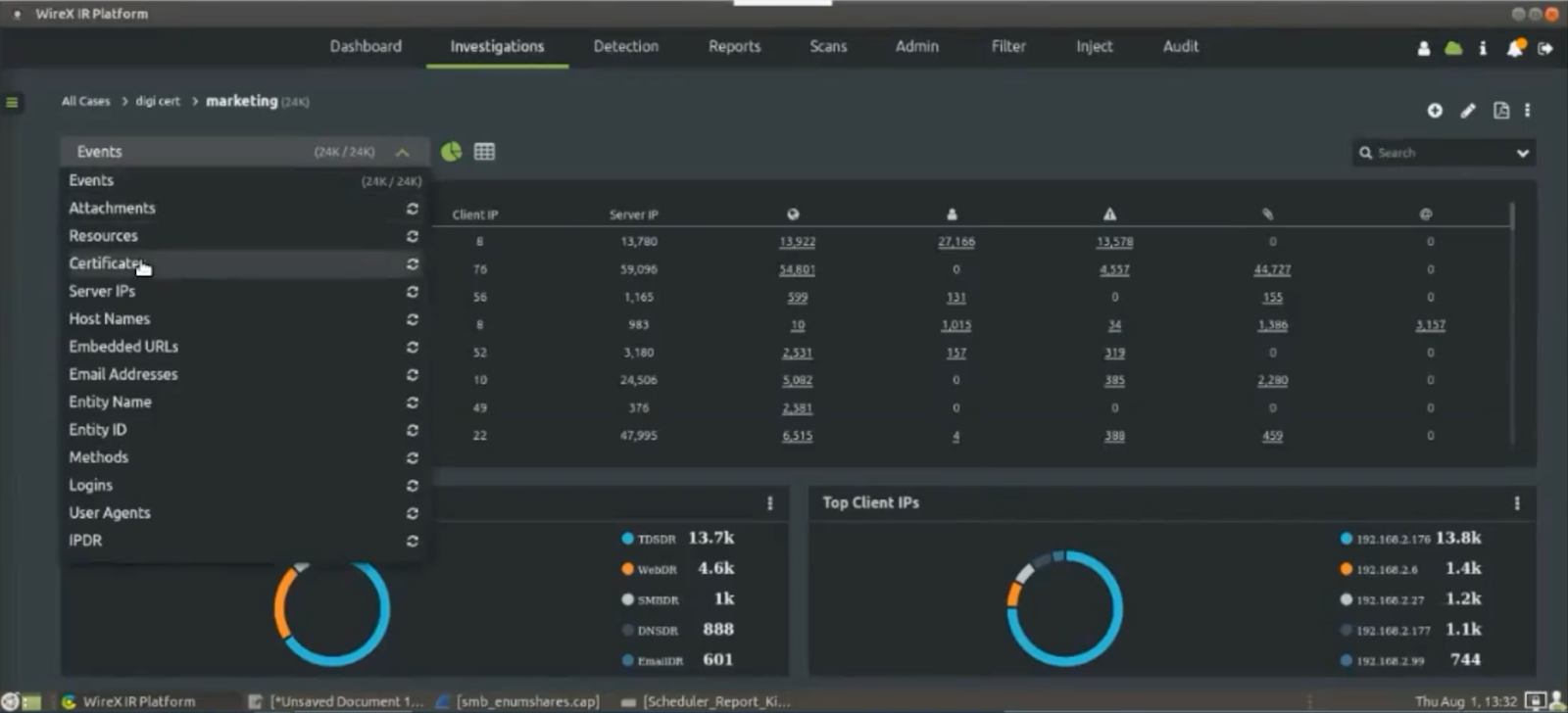
From here, the agent can see their top clients, their IP addresses, top events, top host names and the top certificates that were moved around the network during that time period. As you can see, two DigiCert certificates were observed on this segment in this timeframe.
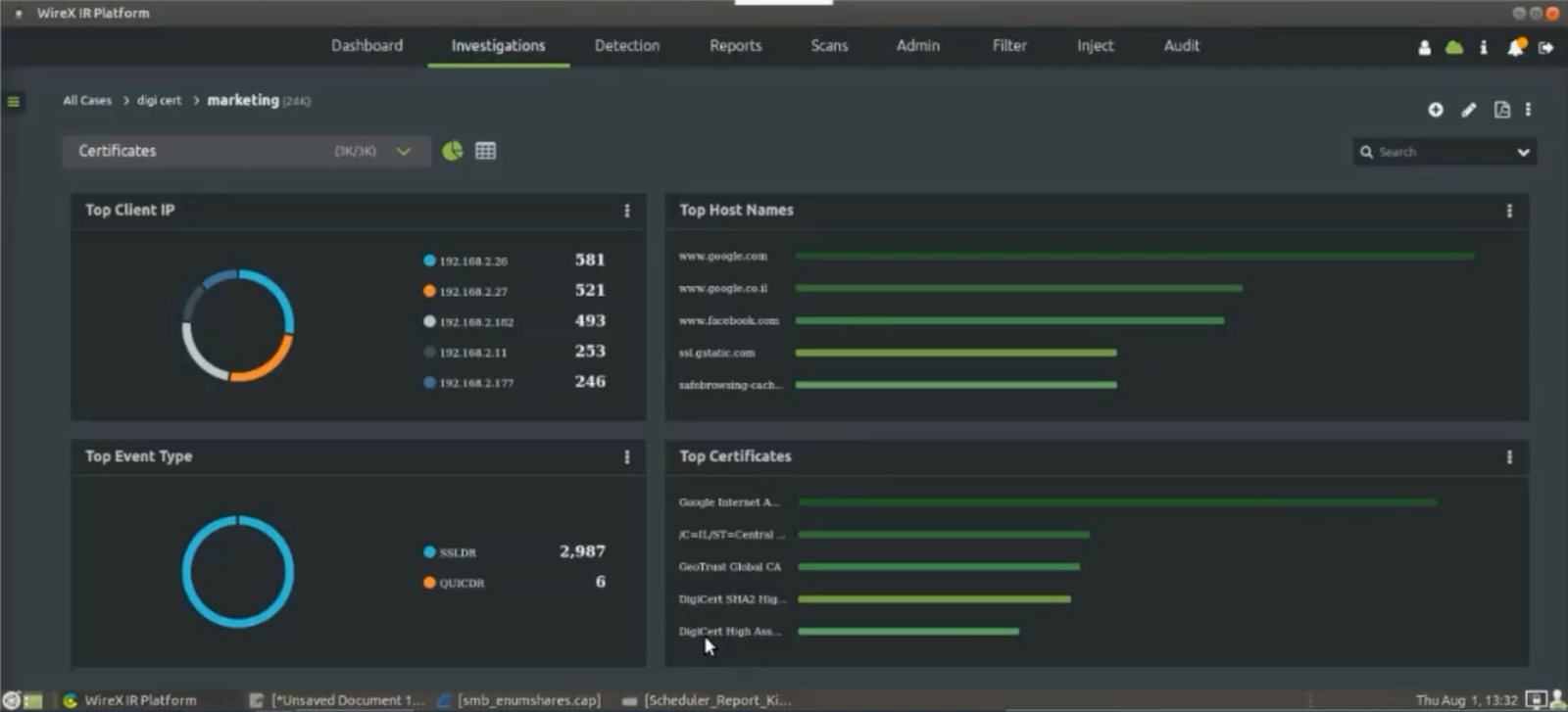
The agent can then do a partial scan search on “digi” and quickly see all of the DigiCert certificates that traversed the network over the last six months. The operator can also see the certificates “from” and “to” dates and then drill down further and see the actual certificate itself. This removes all the guessing. The agent simply says “show me all the DigiCerts that moved during the timeframe I specified”.
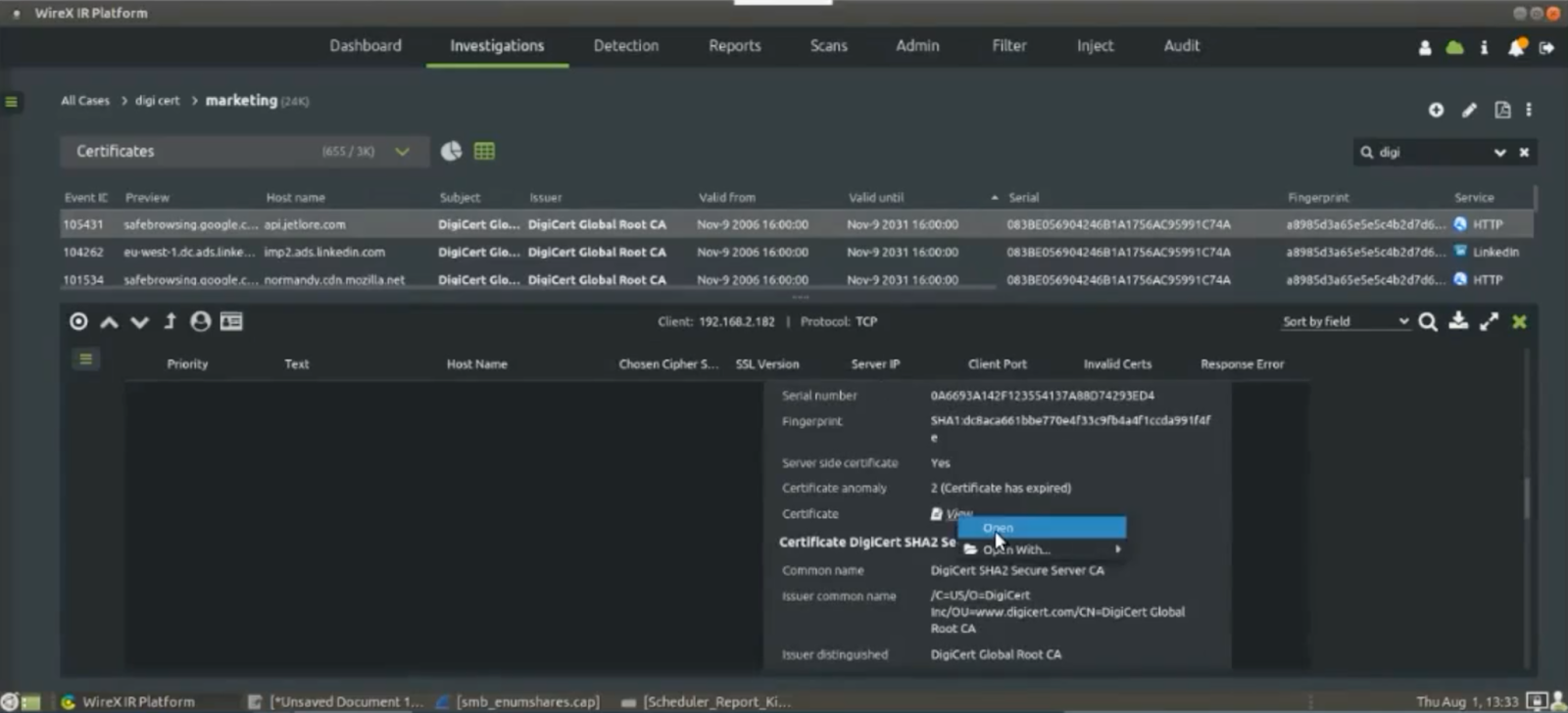
That’s how quickly an agent can do an investigation and dig in. And in this example, the agent was able to quickly see that there are 655 certificates that they need to address.
And just like in the real-life DigiCert example, no one knew they would need this data six months ago. WireX Systems is continuously monitoring and indexing the network passively for situations just like this. The Ne2ition platform is built on our proprietary technology called Contextual CaptureTM that extracts all the network payload information and keeps the data for extended periods of time…up to 12 months in many cases, which is longer than any other network intelligence solution on the market.
As DigiCert released more details with specific serial numbers, organizations were able to scope their exposure to determine if their own certificates were affected. With WireX Systems Ne2ition Platform analysts could query for specific serial numbers and determine the scope of usage over the last 12 months very quickly enabling teams to build a prioritized approach to ensure the most critical systems were not impacted.
What can you do in the future to prevent the DigiCert issue?
Organizations using best practices are always better equipped to quickly assess and respond to situations that arise. Let’s look at some of these best practices and why they matter.
The Importance of Monitoring Digital Certificates
In today’s digitally-driven world, the importance of monitoring digital certificates cannot be overstated. Digital certificates play a crucial role in securing communications, verifying identities, and ensuring data integrity across networks. Understanding which systems use encryption, what the full pedigree of each certificate is, when active certificates will expire, and identifying any expired or expiring certificates in use are essential components of maintaining a robust security posture.
Why Digital Certificates Matter
Digital certificates, often issued by trusted Certificate Authorities (CAs), are used to establish secure connections between clients and servers. They encrypt data transmitted over the internet, ensuring that sensitive information remains confidential and protected from unauthorized access. Without proper encryption, data can be intercepted and exploited, leading to potential breaches and severe consequences for organizations.
Tracking Certificate Expiration
Certificates come with a validity period, after which they expire and need to be renewed. Monitoring the expiration dates of active certificates is crucial to prevent lapses in security. An expired certificate can lead to untrusted connections, potentially exposing sensitive data to threats. Regularly tracking certificate expiration dates ensures timely renewals and uninterrupted secure communications.
Identifying Expired Certificates
Despite best efforts, expired certificates can sometimes go unnoticed. Using expired certificates can break encryption, making the data vulnerable to interception. Continuous monitoring helps in promptly identifying and replacing expired certificates, thereby maintaining the integrity and security of encrypted pathways.
Evaluating Proper Use of Encryption
Maintaining the proper use of encryption involves more than just deploying certificates. It requires a proactive approach to track and evaluate the usage of encryption technologies. This includes:
- Regular Audits: Conducting regular audits of all certificates in use to ensure they adhere to the latest security standards.
- Automated Monitoring Tools: Implementing automated tools to monitor certificate status and send alerts before expiration.
- Updating Encryption Protocols: Keeping encryption protocols up-to-date with current technologies to protect against emerging threats.
- Training and Awareness: Educating staff about the importance of digital certificates and proper encryption practices.
Conclusion
In summary, the importance of monitoring digital certificates extends beyond mere compliance. It is a vital practice for safeguarding sensitive information, maintaining trust, and ensuring the integrity of encrypted communications. By understanding encryption pathways, tracking certificate expiration dates, identifying expired certificates, and evaluating the use of encryption, organizations can fortify their security posture and mitigate risks effectively.
Proactive monitoring and management of digital certificates are essential components of a comprehensive cybersecurity strategy, enabling organizations to stay ahead of potential threats and maintain robust data protection standards. Organizations with visibility into the certificates operating on their network were able to react quickly to DigiCerts announcement and reassure stakeholders with minimized risk to business operations. Using comprehensive network visibility will ensure that your organization is prepared for the next urgent press release.
References
¹DigiCert Revocation Incident







